These solutions will launch the Windows 10 Upgrade in a zero touch setup. While these will certainly start the upgrade process, I do recommend uninstalling AV, DLP, and other security programs that may interfere with the upgrade. If you’re doing this in an enterprise environment, just make sure you test your security software and settings with the upgrade process.
Also, if in an enterprise environment, I suggest disabling power management and screensavers, and creating your own splash screen to cover the initial Microsoft splash (if you’re clever, just create a nice splash with animation and automation…and run the setup.exe with /quiet). The MS splash allows the user to cancel the upgrade; you’ll want to prevent users from doing that.
User can cancel
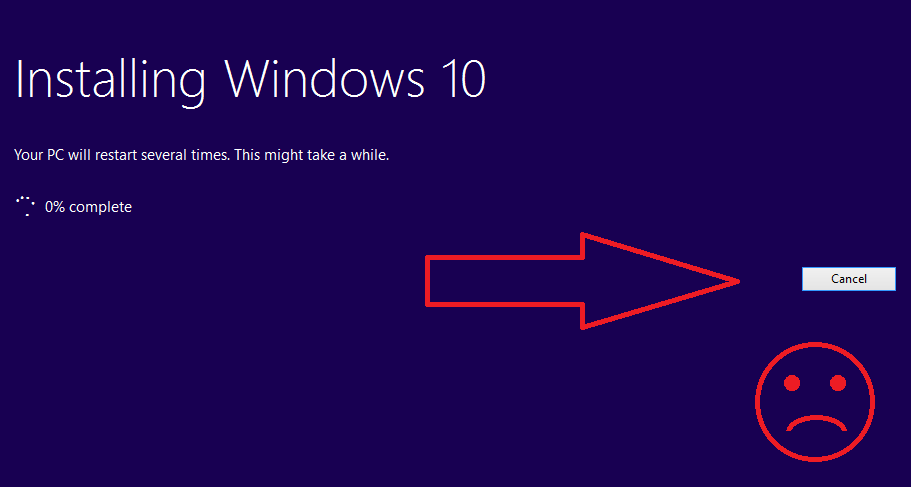
Windows 10 Upgrade Command
This is a single command you can run in your scripts, on SCCM, or LANDesk that will automatically begin the upgrade process—in a zero touch setup.
SCCM
setup.exe /auto upgrade /quiet /copylogs %SystemDrive%\Logs\
setup.exe [/Auto:Upgrade | /Unattend:\\ServerName\ShareName\unattend.xml] /DynamicUpdate Disable /Copylogs %SystemDrive%\Logs\
LANDesk
1.) Download the Win10 ISO, once downloaded extract the contents to your LANDesk file server.
2.) Next you’re going to need the unattend.xml that’s attached. You cannot add or remove anything from this file – only the auto upgrade can be in here. save it to your fileserver in the same location as the extracted setup.exe.
Note – the installer is fully silent with the only UI being the one below. If you wish to change this, edit the .xml to what you require.
3.) Create a distribution task within LANDesk and point to the setup.exe within the windows 10 iso package for your primary file e.g. \\yourlandeskshare\images\Win10Images\Windows 10 OS\setup.exe
Within the Install/Uninstall options, use the following switches /Auto:Upgrade /Unattend:unattend.xml /DynamicUpdate Disable /Copylogs %SystemDrive%\ProgramData\LANDESK\Logs\
4.) Add all of the windows 10 media and unattend.xml as additional files.
5.) Schedule the task and install just as you would any other software. Make sure to use Download and Execute Settings.
Windows 10 PowerShell Script
This is the PowerShell code that does exactly what the single command does.
$scriptPath = split-path -parent $MyInvocation.MyCommand.Definition
$unattend = “””” + $scriptPath + “\unattend.xml” + “”””
$mount = Mount-DiskImage -ImagePath ($scriptpath + “\SW_DVD5_Win_Pro_10.ISO”) -PassThru
$driveLetter = ($mount | Get-Volume).DriveLetter
$setup = $driveLetter + “:\setup.exe”
$param = “/Auto:Upgrade /Unattend:$unattend /DynamicUpdate Disable”
Start-Process -FilePath $setup -WorkingDirectory ($driveLetter + “:\”) -ArgumentList $param
Contents of unattend.xml
You’ll need to point the setup to use this unattend.xml file. Make sure you don’t add anything else to it.
<UpgradeData>
<Upgrade>true</Upgrade>
<WillShowUI>Never</WillShowUI>
</UpgradeData>
Note: <ProductKey>xxxxx-xxxxx-xxxxx-xxxxx-xxxxx</ProductKey>
What the Upgrade Looks Like (after auto reboot)
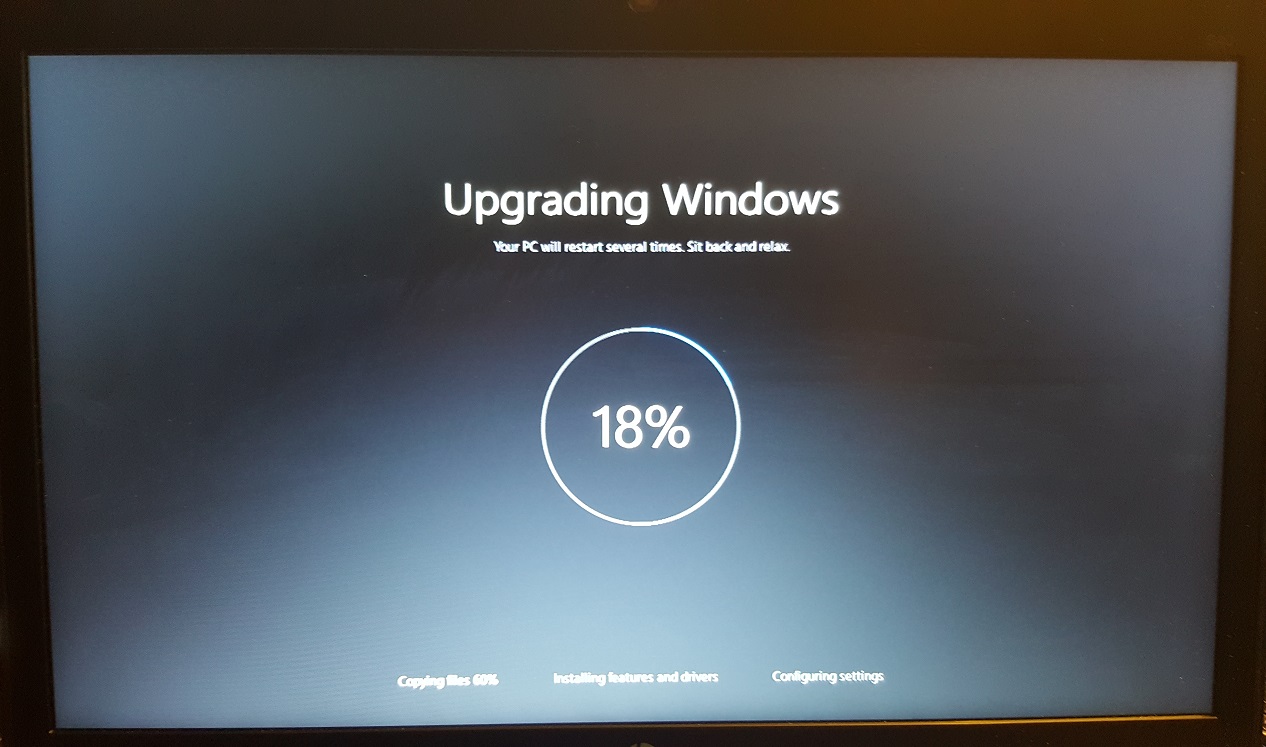
The setup.exe command from SCCM
(for my own reference)
SETUP.EXE” /ImageIndex 3 /auto Upgrade /quiet /noreboot /postoobe “C:\Windows\SMSTSPostUpgrade\SetupComplete.cmd” /postrollback “C:\Windows\SMSTSPostUpgrade\SetupRollback.cmd” /DynamicUpdate Disable /pkey AAAAA-BBBBB-CCCCC-DDDDD-EEEEE /compat IgnoreWarning
If There Are Problems
Disable (preferably uninstall) your Antivirus utility before attempting the upgrade.
- Disable General USB Devices (example – Smart Card Reader).
- Do a clean boot and try again.
- If you are upgrading using the .ISO file, disconnect from the Internet during setup, if you are connected by LAN (Ethernet) or Wi-Fi, disable both and attempt setup again.
- If you are updating through Windows Update, when the download reaches 100% disconnect from the Internet LAN (Ethernet) or Wi-Fi and proceed with the installation.
- If that does not work, try using the .ISO file to upgrade if possible.
- If you are connected to a domain, switch to a local account
- If you have any external devices attached to the machine, disconnect them (example, USB keys, external hard disk, printers, non-essential devices).
- Remove USB flash drives, discs from the DVD/CD player, and other peripheral devices.
Example of Symantec Issue

If you don’t uninstall the Symantec AV, at least upgrade to 12.1.6.1 with the following command line switches: setup /v”/l*v c:\log.txt MIGRATIONDELAY=1 MAXMIGRATIONDELAY=1″
Reference
https://technet.microsoft.com/en-us/library/cc722011(v=ws.10).aspx
https://community.landesk.com/docs/DOC-39519
https://support.symantec.com/en_US/article.TECH231349.html
Notes
The following command line arguments can be used to modify the behavior of Windows installation:
Switch: /auto
Parameters: Upgrade; DataOnly; Clean
Action: Automate install with migration choice for the installation. The media setup UI and progress screens are shown by default, but are automated. This switch also assumes the following default configurations: EULA acceptance, Dynamic Update is enabled, telemetry collection and upload opt – in, OOBE will be skipped, PBR will be updated or created.
Example: setup.exe /auto upgrade
Switch: /quiet
Parameters : N /A
Action: The quiet flag will suppress any setup UX, including rollback UX
Example: setup.exe /auto upgrade /quiet
Switch: /pkey
Parameters: 5×5 product key
Action: Supplies setup with the specified product key. This parameter is not necessary when upgrading with volume licensed media or media that contains a pid.txt in the sources folder.
Example: setup.exe /auto upgrade /pkey ABC12-DEF34-GHI56-JKL78-MNP90
Switch: /showoobe
Parameters: Full; None
Action: When /showoobe is set to Full, the end user must interactively complete OOBE.
Alternatively, when /showoobe is set to None, OOBE is skipped and components are set to their default settings.
Example: setup.exe /auto upgrade /showoobe full
Switch: /noreboot
Parameters: N /A
Action: Setup will not automatically reboot the PC when it completes down – level OS tasks.
The next time the PC is rebooted, setup will continue.
Example: setup.exe /auto upgrade /noreboot
Switch: /DynamicUpdate
Parameters: Enable; Disable
Action: Specifies whether setup will perform Dynamic Update operations (search, download, and install updates).
Example: setup.exe /auto upgrade /DynamicUpdate disable
Switch: /Postoobe Path\setupcomplete.cmd
Parameters: Local file path or UNC network path to a file named setupcomplete.cmd
Action: Injects setupcomplete.cmd file from the specified location. Setupcomplete.cmd is a customized script to perform tasks after the installation completes but before first user login. It is run with System privileges.
Example: setup.exe /auto upgrade /postoobe c:\script\setupcomplete.cmd
Switch: /Postrollback
Parameters : Local file path or UNC network path to a file named setuprollback.cmd
Action: Injects setuprollback.cmd file from the specified location. Setuprolback.cmd is a customized script to perform tasks after the installation fails and the PC has rolled back to its previous OS. It is run with the same privileges as the user or process that launched setup.
Example: setup.exe /auto upgrade /postrollback \MyShare\script\setuprollback.cmd
Switch: /installfrom
Parameters: Local file path or network path to a specific.wim
Action: Specifies location for installation source media /files
Example: setup.exe /auto clean /installfrom d:\myWim\customwim.wim
Switch: /PBRUpdate
Parameters: Enable; Disable
Action: When /PBRUpdate is set to Enable, setup will update or create the PBR partition.
Conversely, when /PBRUpdate is set to Disable, setup will not update or create the PBR partition
Example: setup.exe /auto upgrade /PBRupdate disable
Switch: /migratealldrivers
Parameters: All; None
Action: When /migratealldrivers is set to All, setup will attempt to migrate all drivers as part of the installation. In contrast, when /migratealldrivers is set to None, setup will not migrate any drivers as part of the installation. NOTE: this switch should only be used in testing and test envoriments.It should not be used in production.
Example: setup.exe /auto upgrade /migratealldrivers none
Switch: /installdrivers
Parameters: Local file path or UNC network path to a folder that contains.inf files
Action: Setup will inject all driver.infs found in the specified location during the installation process. Setup will recursively search through all the subfolders of the specified location.
Example: setup.exe /auto upgrade /installdrivers c:\myUpgrade\drivers
Switch: /Telemetry
Parameters: Enable; Disable
Action: When /Telemetry is set to Enable, setup will collect and upload telemetry generated by the installation. However, when /Telemetry is set to Disable, setup will not collect and upload installation – related telemetry.
Example: setup.exe /auto upgrade /Telemetry enable
Switch: /copylogs
Parameters: Local file paths and UNC network paths
Action: Upon failure, setup will copy or upload compressed logs to the specified location.
Please note that the PC and /or user must have permission and network access to the specified file path. This command runs in the system context so may not have permissions to copy to locations that require user permissions
Example: setup.exe /auto upgrade /copylogs \MyShare\UpgradeLogs
Here are some usage examples.
An admin wants to upgrade the department’s PCs from Windows 7 Enterprise overnight. He does not want the setup user interface to appear, but he does want the end users to manually go through the Out of box experience(known as OOBE) experience.
The following command line can be used to orchestrate the full upgrade to Windows Next, requiring user input only once the machine reaches OOBE:
Setup.exe /auto upgrade /quiet /showoobe full
Alternatively, a deployment engineer may want to collect logs and other diagnostic information from test PCs in the event of a failure.
The following command line instructs setup invoke the setuprollback.cmd script after an installation failure:
Setup.exe /auto upgrade /installdrivers c:\myUpgrade\drivers /postrollback c:\setuprollback.cmd