What is ransomware?
Ransomware stops you from using your PC. It holds your PC or files for ransom.
Some versions of ransomware are called “FBI Moneypak” or the “FBI virus” because they use the FBI’s logos.
What does it look like and how does it work?
There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC.
They can:
- Prevent you from accessing Windows.
- Encrypt files so you can’t use them.
- Stop certain apps from running (like your web browser).
They will demand that you do something to get access to your PC or files. We have seen them:
- Demand you pay money.
- Make you complete surveys.
Often the ransomware will claim you have done something illegal with your PC, and that you are being fined by a police force or government agency.
These claims are false. It is a scare tactic designed to make you pay the money without telling anyone who might be able to restore your PC.
There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Prevalent ransomware
Locky and Cerber are two of the most prevalent and dangerous ransomware currently active.
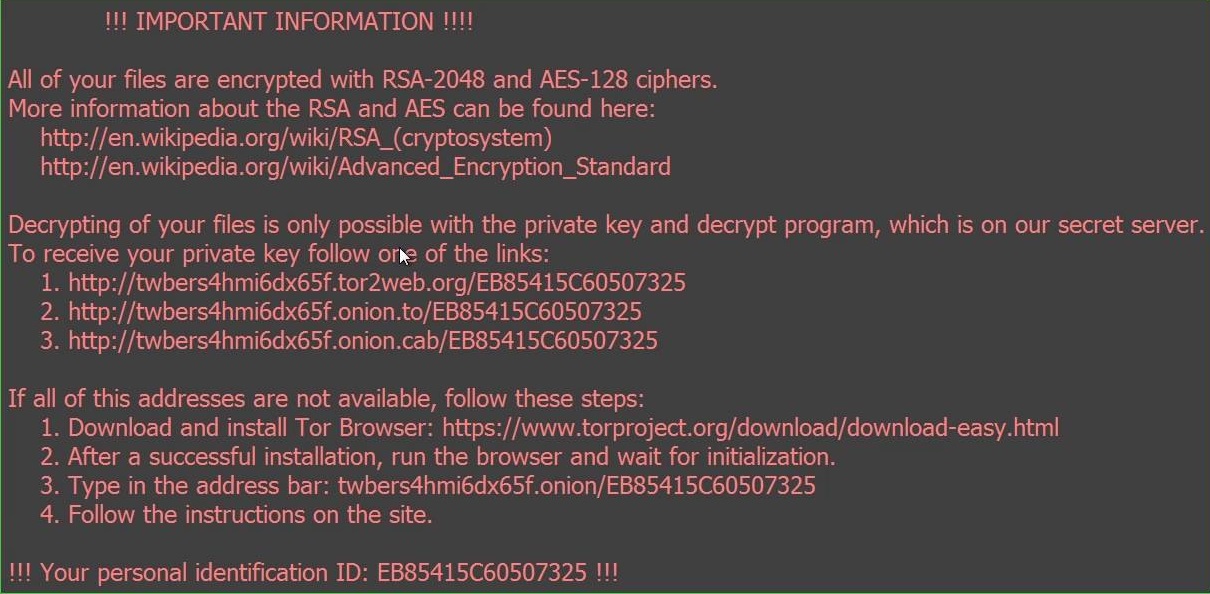
Locky Recovery Notice
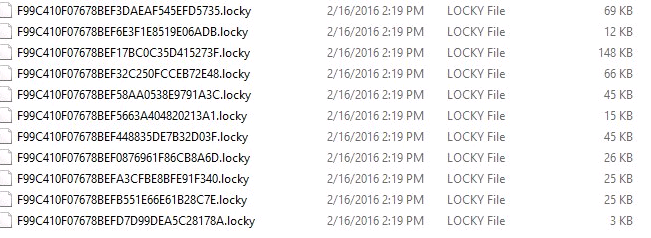
What the Locky encrypted files look like
Detection
So, with Locky on the rise, it got me thinking, what exactly does Locky (and other ransomware) do to your computer? What happens when the ransomware starts processing? Most ransomware—that encrypts files—uses something known as CryptoLocker, which uses a form of AES encryption. Even before Locky starts encrypting files, EXEs are added to folders, and registry keys are added to the registry.
Soo…how do we prevent or at least reduce the impact of ransomware? A simple approach would just be to monitor the computer for ransomwarelike behavior.
Something I came of up with—which is still early in development—is to scan all the known areas that Locky is likely to hit first. This would include common registry keys, EXEs in the user’s Local and Roaming folders, and monitoring ‘marker’ files. A marker file is just a text file in the user’s profile…which has a specific hash number associated with it. If that marker file disappears, is encrypted, or is changed in any way, a script changes from monitoring mode, to alert mode. Likewise, if known ransomware registry keys are detected, a script goes into alert mode. The idea is to create a monitoring script, with low impact to system resources, that will act as a method for early detection. Early detection means less of the files will be encrypted.
This is the start of my script – this would be compiled and ran as a silent process
@echo off
title Ransomware Scanner
color 0a
:: booValean set to false
set booVal=FALSE
:: reg key to check
set regKey=CryptoLocker
:: file marker name
set fileName=DO_NOT_DELETE
:: file extensions to check
set fileType1=.EXE
set fileType2=.exe
set fileType3=.locky
:: md5 to check
set md5=1914255e58188f70feced69533c99aec
Setlocal EnableDelayedExpansion
set timer=timeout /t 10
C:
cd C:\Users\%username%\AAA
:LOOP
:: CHECK FOR CRYPTOLOCKER REG KEY
cls
Echo Scanning computer for ransomware...Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
FOR /F "tokens=1" %%A IN ('REG QUERY "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run"') DO (
if %%A==%regKey% set booVal=TRUE
)
%timer%>nul
:: CHECK FOR CRYPTOLOCKER REG KEY
cls
Echo Scanning computer for ransomware...Checking HKCU\SOFTWARE\CryptoLocker
REG QUERY HKCU\SOFTWARE\CryptoLocker
IF %errorlevel%==0 GOTO :END
:: CHECK FOR CRYPTOLOCKER_0388 REG KEY
cls
Echo Scanning computer for ransomware...Checking HKCU\SOFTWARE\CryptoLocker_0388
REG QUERY HKCU\SOFTWARE\CryptoLocker_0388
IF %errorlevel%==0 GOTO :END
:: CHECK FOR CRYPTOLOCKER REG KEY
cls
Echo Scanning computer for ransomware...Checking HKCU\SOFTWARE\Locky
REG QUERY HKCU\SOFTWARE\Locky
IF %errorlevel%==0 GOTO :END
:: CHECK FOR EXE IN THE LOCAL FOLDER
cls
Echo Scanning computer for ransomware...Checking Local Folder
for /F "tokens=*" %%U IN ('dir /b C:\Users\%username%\AppData\Local') do (
if [%%~xU]==[%fileType1%] set booVal=TRUE
if [%%~xU]==[%fileType2%] set booVal=TRUE
)
%timer%>nul
if %booVal% EQU TRUE goto :END
:: CHECK FOR EXE IN THE ROAMING FOLDER
cls
Echo Scanning computer for ransomware...Checking Roaming Folder
for /F "tokens=*" %%V IN ('dir /b C:\Users\%username%\AppData\Roaming') do (
if [%%~xV]==[%fileType1%] set booVal=TRUE
if [%%~xV]==[%fileType2%] set booVal=TRUE
)
%timer%>nul
if %booVal% EQU TRUE goto :END
:: CHECK FOR EXE IN THE DOCUMENT FOLDER
cls
Echo Scanning computer for ransomware...Checking C:\Users\%username%\Documents
for /F "tokens=*" %%W IN ('dir /b C:\Users\%username%\Documents') do (
if [%%~xW]==[%fileType3%] set booVal=TRUE
)
%timer%>nul
if %booVal% EQU TRUE goto :END
:: CHECK FOR EXE IN THE PICTURES FOLDER
cls
Echo Scanning computer for ransomware...Checking C:\Users\%username%\Pictures
for /F "tokens=*" %%X IN ('dir /b C:\Users\%username%\Pictures') do (
if [%%~xX]==[%fileType3%] set booVal=TRUE
)
%timer%>nul
if %booVal% EQU TRUE goto :END
:: CHECK TO SEE IF AAA FILE EXISTS
cls
Echo Scanning computer for ransomware...Checking AAA_%fileName%.txt
if not exist C:\Users\%username%\AAA\AAA_%fileName%.txt set booVal=TRUE
%timer%>nul
if %booVal% EQU TRUE goto :END
:: CHECK TO SEE IF BMP FILE EXISTS
cls
Echo Scanning computer for ransomware...Checking %UserpProfile%\Desktop\_Locky_recover_instructions.bmp
if exist %UserpProfile%\Desktop\_Locky_recover_instructions.bmp set booVal=TRUE
%timer%>nul
if %booVal% EQU TRUE goto :END
:: RETURN AAA FILE CHECKSUM
cls
Echo Scanning computer for ransomware...Checking MD5 on AAA_%fileName%.txt
set count=1
for /F "tokens=* delims=" %%Y IN ('CertUtil -hashfile C:\Users\%username%\AAA\AAA_%fileName%.txt MD5') do (
set var!count!=%%Y
set /a count+=1
)
if %booVal% EQU TRUE goto :END
:: CHECK TO SEE IF MD5 IS THE SAME -- IF NOT EQUAL, SET TRUE
:: removes spaces
set var2=%var2: =%
if %var2% NEQ %md5% set booVal=TRUE
%timer%>nul
if %booVal% EQU TRUE goto :END
CLS
echo Old MD5: %var2%
echo New MD5: %md5%
echo Detect: %booVal%
%timer%>nul
goto :LOOP
:END
CLS
echo Old MD5: %var2%
echo New MD5: %md5%
echo Detect: %booVal%
echo.
echo msgbox " Ransomware has been detected^!" > "%temp%\popup.vbs"
wscript.exe "%temp%\popup.vbs"
set booVal=FALSE
goto :LOOP
Notes
https://blog.malwarebytes.org/threat-analysis/2016/03/look-into-locky/
http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information