What is a macro and what is the security risk?
Macros automate frequently-used tasks; many are created with VBA and are written by software developers. However, some macros pose a potential security risk. A person with malicious intent can introduce a destructive macro, in a document or file, which can spread a virus on your computer.
Use these registry keys to disable macros—one machine at a time.
Word
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Security]
“VBAWarnings”=dword:00000004
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Security\FileBlock]
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Security\FileBlock\OoxmlConverters]
“{A5C79653-FC73-46ee-AD3E-B64C01268DAA}”=dword:00000000
Excel
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Excel\Security]
“VBAWarnings”=dword:00000004
PowerPoint
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\PowerPoint\Security]
“VBAWarnings”=dword:00000004
What this setting looks like under File, Options, Trust Center, Trust Center Settings, Macros in the respective app.
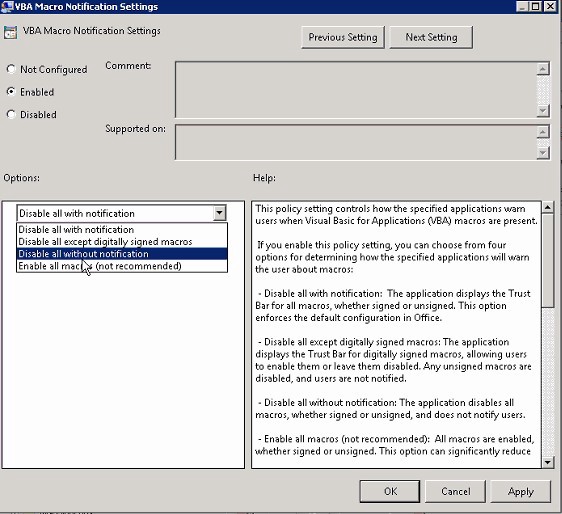
Notes
You may of course need to do this for a fleet of computers. The best way to handle that is through Group Policy. See https://www.microsoft.com/en-us/download/details.aspx?id=35554
User Configuration/Administrative Templates/Microsoft Office VERSION 20VERSION/Application Settings/Security/Trust Center/Trusted Locations
As a secondary enterprise solution, you could also deploy a script to disable the macros—cycling through each user reg hive and applying the appropriate reg keys. Note, this will not prevent someone from re-enabling them, but will at least turn them off.
The script I created is below. The magic happens when each user SID is loaded and the reg keys are applied.
on error resume next
Set objShell = CreateObject("Wscript.Shell")
Set objFSO = CreateObject("Scripting.FileSystemObject")
strComputer = "."
strCurrentDirectory = objShell.CurrentDirectory
Const HKEY_LOCAL_MACHINE = &H80000002
Const OverwriteExisting = TRUE
Const POPUP_TITLE = "User To SID Conversion"
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set objRegistry=GetObject("winmgmts:\\" & strComputer & "\root\default:StdRegProv")
strKeyPath = "SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\ProfileList"
objRegistry.EnumKey HKEY_LOCAL_MACHINE, strKeyPath, arrSubkeys
For Each objSubkey In arrSubkeys
'on error resume next
strValueName = "ProfileImagePath"
strSubPath = strKeyPath & "\" & objSubkey
objRegistry.GetExpandedStringValue HKEY_LOCAL_MACHINE,strSubPath,strValueName,strValue
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set objAccount = objWMIService.Get("Win32_SID.SID='" & objSubkey & "'")
strUser = objAccount.AccountName
'strDomain = objAccount.ReferencedDomainName'returns referenced domain
'DISPLAY PROFILE NAME & SID
objSubkey = trim(objSubkey)'trims whitespace
strUser = trim(strUser)'trims whitespace
'msgbox "objSubkey: " & objSubkey'returns SID
'msgbox strUser'returns username
'LOGIC TO DETERMINE IF REGISTRY ACCOUNT IS TO BE LOADED
if strUser = "SYSTEM" then strUser=""
if strUser = "LOCAL SERVICE" then strUser=""
if strUser = "NETWORK SERVICE" then strUser=""
'if strUser = "ADMINISTRATOR" then strUser=""
if strUser <> "" then
on error resume next
'msgbox objSubkey
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\16.0\Word\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\16.0\Word\Security\FileBlock\OoxmlConverters"" /v {A5C79653-FC73-46ee-AD3E-B64C01268DAA} /d 00000000 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\16.0\Excel\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\16.0\PowerPoint\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\15.0\Word\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\15.0\Word\Security\FileBlock"" /v {A5C79653-FC73-46ee-AD3E-B64C01268DAA} /d 00000000 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\15.0\Excel\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\15.0\PowerPoint\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f /reg:64",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\14.0\Word\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\14.0\Word\Security\FileBlock"" /v {A5C79653-FC73-46ee-AD3E-B64C01268DAA} /d 00000000 /t REG_DWORD /f",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\14.0\Excel\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f",0,true
objShell.Run "cmd /c reg.exe add ""HKEY_USERS\" & objSubkey & "\Software\Microsoft\Office\14.0\PowerPoint\Security"" /v VBAWarnings /d 00000004 /t REG_DWORD /f",0,true
end if
Next
Reference