WARNING: This is experimental
For any of those interested, this is the SetupComplete CMD file Microsoft uses to complete the Task Sequence during a Windows 7-8 upgrade to Windows 10.
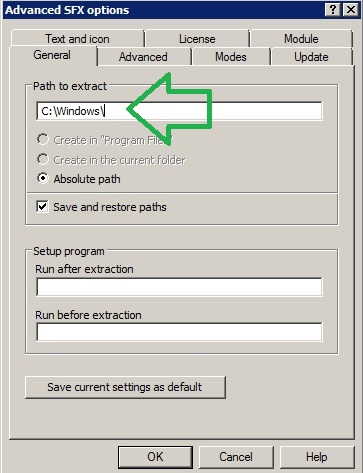
It is located here: C:\Windows\SMSTSPostUpgrade
The importance of this file is that it manages whether or not a rollback will happen (failures in the task sequence), along with controlling some bootstrap tasks. You could add to this—-at the very end of the file—if you wanted to accomplish something post—post setup.
You can append to the file using three methods:
#1 Just create a package that runs and overwrites the file (a copy command sorta thing).
#2 Add a Run Command into the Task Sequence and echo to the SetupComplete file; remember to use ‘>>’ and not just ‘>’
Example
echo DO THIS >> C:\Windows\SMSTSPostUpgrade\SetupComplete.cmd
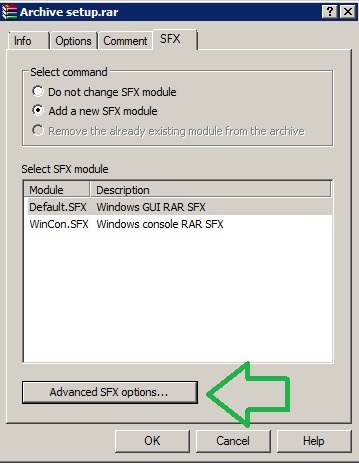
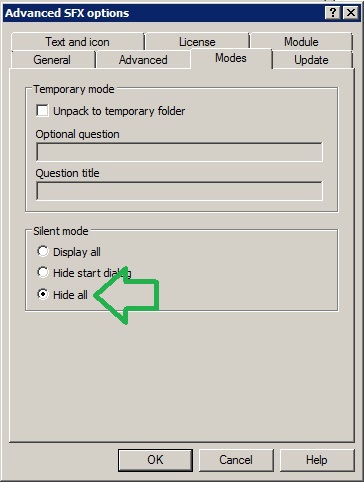
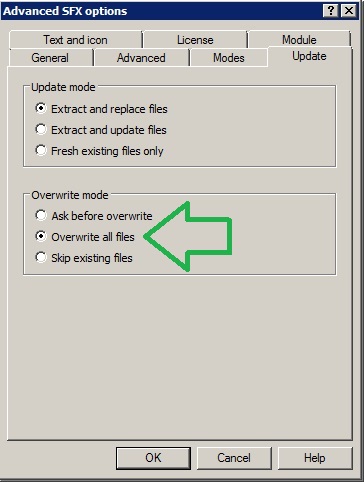
#3 Create a self-extracting EXE (I like using WINRAR) to just overwrite the file (no copy command needed).
The Script
@ECHO OFF
REM SCCMClientPath should be set before we get here
REM This script is written by ConfigMgr Task Sequence Upgrade Operating System action
REM SetupComplete.cmd — Upgrade Complete, calling TSMBootstrap to resume task sequence
echo %DATE%-%TIME% Entering setupcomplete.cmd >> C:\Windows\setupcomplete.log
echo %DATE%-%TIME% Setting env var _SMSTSSetupRollback=FALSE >> C:\Windows\setupcomplete.log
set _SMSTSSetupRollback=FALSE
echo %DATE%-%TIME% Setting registry to resume task sequence after reboot >> C:\Windows\setupcomplete.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupType /t REG_DWORD /d 2 /f
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v CmdLine /t REG_SZ /d “C:\Windows\SMSTSPostUpgrade\setupcomplete.cmd” /f
echo %DATE%-%TIME% Running C:\Windows\CCM\\TSMBootstrap.exe to resume task sequence >> C:\Windows\setupcomplete.log
C:\Windows\CCM\\TSMBootstrap.exe /env:Gina /configpath:C:\_SMSTaskSequence /bootcount:2
IF %ERRORLEVEL% EQU -2147021886 (
echo %DATE%-%TIME% ERRORLEVEL = %ERRORLEVEL% >> C:\Windows\setupcomplete.log
echo %DATE%-%TIME% TSMBootstrap requested reboot >> C:\Windows\setupcomplete.log
echo %DATE%-%TIME% Rebooting now >> C:\Windows\setupcomplete.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupShutdownRequired /t REG_DWORD /d 1 /f
) else (
echo %DATE%-%TIME% ERRORLEVEL = %ERRORLEVEL% >> C:\Windows\setupcomplete.log
echo %DATE%-%TIME% TSMBootstrap did not request reboot, resetting registry >> C:\Windows\setupcomplete.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupType /t REG_DWORD /d 0 /f
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v CmdLine /t REG_SZ /d “” /f
)
echo %DATE%-%TIME% Exiting setupcomplete.cmd >> C:\Windows\setupcomplete.log
set SCCMClientPath=
Notes
To understand more about these files, look in the C:\Windows\CCM folder. There are file templates in there which are used to generate these setup cmds (SetupCompleteTemplate.cmd
SetupRollbackTemplate.cmd).
What the SetupRollback.cmd looks like (located in the same place as the SetupComplete.cmd)
@ECHO OFF
REM SCCMClientPath should be set before we get here
REM This script is written by ConfigMgr Task Sequence Upgrade Operating System action
REM SetupRollback.cmd — Upgrade Rolled back, calling TSMBootstrap to resume task sequence
echo %DATE%-%TIME% Entering setuprollback.cmd >> C:\Windows\setuprollback.log
echo %DATE%-%TIME% Setting env var _SMSTSSetupRollback=TRUE >> C:\Windows\setuprollback.log
set _SMSTSSetupRollback=TRUE
echo %DATE%-%TIME% Setting registry to resume task sequence after reboot >> C:\Windows\setuprollback.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupType /t REG_DWORD /d 2 /f
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v CmdLine /t REG_SZ /d “C:\Windows\SMSTSPostUpgrade\setuprollback.cmd” /f
echo %DATE%-%TIME% Running C:\Windows\CCM\\TSMBootstrap.exe to resume task sequence >> C:\Windows\setuprollback.log
C:\Windows\CCM\\TSMBootstrap.exe /env:Gina /configpath:C:\_SMSTaskSequence /bootcount:2
IF %ERRORLEVEL% EQU -2147021886 (
echo %DATE%-%TIME% ERRORLEVEL = %ERRORLEVEL% >> C:\Windows\setuprollback.log
echo %DATE%-%TIME% TSMBootstrap requested reboot >> C:\Windows\setuprollback.log
echo %DATE%-%TIME% Rebooting now >> C:\Windows\setuprollback.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupShutdownRequired /t REG_DWORD /d 1 /f
) else (
echo %DATE%-%TIME% ERRORLEVEL = %ERRORLEVEL% >> C:\Windows\setuprollback.log
echo %DATE%-%TIME% TSMBootstrap did not request reboot, resetting registry >> C:\Windows\setuprollback.log
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v SetupType /t REG_DWORD /d 0 /f
reg add “HKEY_LOCAL_MACHINE\SYSTEM\Setup” /v CmdLine /t REG_SZ /d “” /f
)
echo %DATE%-%TIME% Exiting setuprollback.cmd >> C:\Windows\setuprollback.log
set SCCMClientPath=