Introduction
The LANDesk Inventory Scanner (LDISCN32.EXE) is able to scan and report back to the Core Server a huge amount of information but time to time collect some more, specific, information from the client is required.
There are basically three different approaches:
Scan for a specific value of the registry
for example this is useful if we know exactly the name and location of the registry value we want to scan for.
The procedure to instruct the Inventory Scanner to retrieve it is quite simple and well covered in the article DOC-1089
Scan for something that is not in the registry
If the value we need to scan for is not directly available in the registry or some manipulations to it are necessary before to acquire it we need to use a different approach.
The idea is to write a script or a program that will run periodically on the device. The program will collect the data and put the result of the execution in a specific registry key of the client.
Then we can use the DOC-1089 to retrieve the values and store them in the inventory.
Scan for information that are not contained in specific registry value and that cannot fit in a single registry value
In some specific cases we need to grab some information that is complex and the result of our script elaboration cannot fit in a single registry value.
A good example for this situation is how to retrieve the all the registry values that are under the Run registry key (HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run ).
How to scan for the full registry key is explained in the article DOC-5709
How can we generalize the method used by the article DOC-5709 ?
To do this we need some background information before to start.
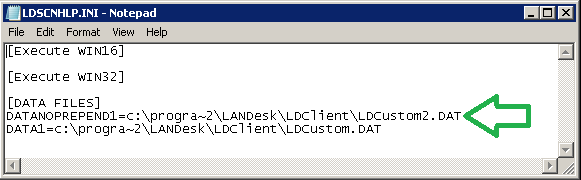
In the client folder directory ( C:\Program Files\LANDesk\LDClient for English OS ) there is the file LDSCNHLP.INI.
This file will tell to the Inventory Scanner two things:
- A program to execute before to start the scan of the device
- Where to catch the output that my program will generate
The file contains generally three sections:
[EXECUTE WIN16]
Not so much used in these days:
In this section we need to list all the programs we want to start on a 16bit platform
[EXECUTE WIN32]
In this section we need to list all the programs we want to start on a 32bit platform
The syntax to use in the EXECUTE section is:
LAUNCH<n>=<compete path of the program to launch>
Where <n> is a sequence number starting from 1
Example
LAUNCH1=C:\Program Files\LANDesk\LDClient\ldcstm32.exe /s
LAUNCH2=C:\Program Files\LANDesk\LDClient\myPersonalScan.exe
Optionally is possible to add the statement TIMEOUT<n>=millisecond to wait before to give up:
Example
LAUNCH1=C:\Program Files\LANDesk\LDClient\ldcstm32.exe /s
TIMEOUT1=600
LAUNCH2=C:\Program Files\LANDesk\LDClient\myPersonalScan.exe
TIMEOUT2=600
[DATA FILES]
In this section we need to specify the name of the file(s) where our program(s) will write the output information
The data needs to be in a particular format that we will cover in the next point.
The syntax to use to specify the files is:
DATA<n>=<compete path of the file that contains the information to add to the inventory>
Where <n> is a sequence number starting from 1
Example
DATA1=C:\PROGRA~1\LANDesk\LDClient\LDCUSTOM.DAT
DATA2=C:\PROGRA~1\LANDesk\LDClient\MyStuff.DAT
The data gathered from the data files needs to be Custom Data and will be stored under the Custom Data node of the inventory
If we want to store the data in other part of the Inventory (for example under the OS node) we need to use the keyword
DataNoPrepend<n>=<compete path of the file that contains the information to add to the inventory>
Where <n> is a sequence number starting from 1.
Format of the data files
The format of the data files is quite simple and resemble the format used in the LDAPPL3.TEMPLATE to scan for registry keys.
The format is:
<node of the inventory> – <node of the inventory> – ….. – <value name> = <the value>
Example
We want to store the information under Custom Data -> My Special node -> Is Working and the value is YES. The file need to contain this line:
Custom Data – My Special node – Is Working = YES
If we want to store something under OS -> RegistryKey -> RunCount and the value of RunCount is 100 we need to have a line like this one:
OS – RegistryKey – RunCount = 100
Note that in this case the file that contains this line needs to be referenced with the keyword DataNoPrepend<n> in the LDSCNHLP.INI file.
Note, if you use DataNoPrepend<n> to read a .DAT file, make sure you press the Enter key to move the cursor to the next line in the .DAT file. Failing to do so will result in the text being only 11 characters long in the inventory scan.
Example
MyAttribute == this is the attribute in the database that I want to populate with a value of 012345678901. This will look like below in my .DAT file
MyAttribute = 012345678901
Without an empty line in the .DAT file, MyAttribute will have only 01234567890
Considerations
The usage of LDSCNHLP.INI extends incredibly the potentiality of the Inventory Scanner but there are some important considerations to keep in mind before to use it:
- Make sure that the program you are calling will not impact too much the CPU of the machine and will not produce any visible output:
If a VbScript or JScript is used, call it with CSCRIPT to be sure that eventually present PRINT calls will not be displayed as modal message boxes.
- Make sure that the program is not asking for any form of input or interaction.
- The program will be executed in the context of the user that is launching the Inventory Scanner.