I wrote this script to run locally on a computer, which will import BitLocker information into Active Directory. There are two caveats,
#1 The security context must be a user that has been delegated access to the OU containing the computer objects.
#2 If you run this from LANDesk, using a service account is recommended (System Account will not work). A better, more reliable option is just to use reg keys. LANDesk has a built-in way of reading specific reg keys from client machines. See the reg key method at the bottom.
No matter what you decide to do, locally retrieving and parsing the BitLocker information isn’t all that difficult. Once you have it, you just have to upload/import it into AD; I just use manage-bde.exe -protectors -adbackup c: -id to accomplish the task.
Local/Service Account Method
@echo off
title Import Bitlocker Recovery Information
cls
Echo Checking Bitlocker compliance…
set MyVar=
rem used for setting path for testing and remote management software
set CurDir=\\%computername%\c$\Users\%username%\Desktop\BitLocker_Compliance
rem example for landesk \\%computername%\c$\Progra~2\LANDesk\LDClient\sdmcache\apps\BitLocker\importer
rem and, make sure you select the script to run under current user – interactive mode
rem the user must have admin rights or access to run manage-bde
setlocal ENABLEDELAYEDEXPANSION
REM PRIMARY EXTRACTION METHOD – RETURNS BITLOCKER ID
for /f “skip=4 tokens=2 delims=:” %%g in (‘”\\%computername%\c$\windows\system32\manage-bde.exe -protectors -get c:“‘) do set MyVar=%%g
\\%computername%\c$\windows\system32\ping.exe -n 10 127.0.0.1>nul
rem new line
cls
Echo Checking BitLocker compliance…done
echo.
Echo Importing Recovery information into AD…
echo.
REM IMPORT BITLOCKER INFO INTO AD USING BITLOCKER ID
\\%computername%\c$\windows\system32\manage-bde.exe -protectors -adbackup c: -id%MyVar% && (
\\%computername%\c$\windows\system32\ping.exe -n 10 127.0.0.1>nul
rem new line
cls
Echo Checking BitLocker compliance…done
echo.
Echo Importing Recovery Information into AD…done
echo.
Echo Updating the Computer Description in AD…
echo.
REM This adds some text into the computer object description in AD
“%CurDir%\compliance.vbs”
\\%computername%\c$\windows\system32\ping.exe -n 10 127.0.0.1>nul
rem new line
cls
Echo Checking BitLocker compliance…done
echo.
Echo Importing Recovery information into AD…done
echo.
Echo Updating Computer Description in AD…done
Echo.
Echo Import completed successfully.
echo.
pause
) || (
cls
echo Failed. Try again, and Run as Administrator.
pause
)
exit /b 0
Reg Key Method
@echo on
SETLOCAL ENABLEDELAYEDEXPANSION
REM CHECK TO SEE IF BITLOCKER DAT FILES ARE MISSING (FROM OUR IMAGING PROCESS)
if not exist \\%computername%\c$\Bitlocker\B1.dat goto :FETCH
:REGKEYS
REM USING DAT FILES, IMPORT BITLOCKER PASSWORDS INTO REGISTRY
if exist \\%computername%\c$\BitLocker\B1.dat (
for /f “tokens=* delims=” %%a in (c:\BitLocker\B1.dat) do set BitPass1=%%a
\\%computername%\c$\windows\system32\reg delete hklm\software\BitPass /v BitPass1 /f /reg:64
\\%computername%\c$\windows\system32\reg add hklm\software\BitPass /v BitPass1 /t REG_SZ /d “!BitPass1!” /f /reg:64
)
if exist \\%computername%\c$\BitLocker\B2.dat (
for /f “tokens=* delims=” %%b in (c:\BitLocker\B2.dat) do set BitPass2=%%b
\\%computername%\c$\windows\system32\reg delete hklm\software\BitPass /v BitPass2 /f /reg:64
\\%computername%\c$\windows\system32\reg add hklm\software\BitPass /v BitPass2 /t REG_SZ /d “!BitPass2!” /f /reg:64
)
REM CLEANUP
del /q C:\BitLocker\drive.dat
del /q C:\BitLocker\B1.dat
del /q C:\BitLocker\B2.dat
REM LAUNCH INVENTORY SCANNER
“C:\Program Files (x86)\LANDesk\LDClient\LDISCN32.EXE” /NTT=YourLANDeskServer.YourDomain.com:5007 /S=YourLANDeskServer.YourDomain.com /I=HTTP://YourLANDeskServer.YourDomain.com/ldlogon/ldappl3.ldz /F /SYNC
exit /b 0
:FETCH
md \\%computername%\c$\BitLocker
REM RETRIEVE BITLOCKER PASSWORDS AND PUT INTO DAT FILE
\\%computername%\c$\windows\system32\manage-bde -protectors -get c: -type recoverypassword>C:\BitLocker\drive.dat
for /f “tokens=*” %%j in (C:\BitLocker\drive.dat) do set KEY1=%%j
echo !KEY1!>c:\Bitlocker\B1.dat
\\%computername%\c$\windows\system32\manage-bde -protectors -get d: -type recoverypassword>C:\BitLocker\drive.dat
for /f “tokens=*” %%k in (C:\BitLocker\drive.dat) do set KEY2=%%k
echo !KEY2!>c:\BitLocker\B2.dat
goto :REGKEYS
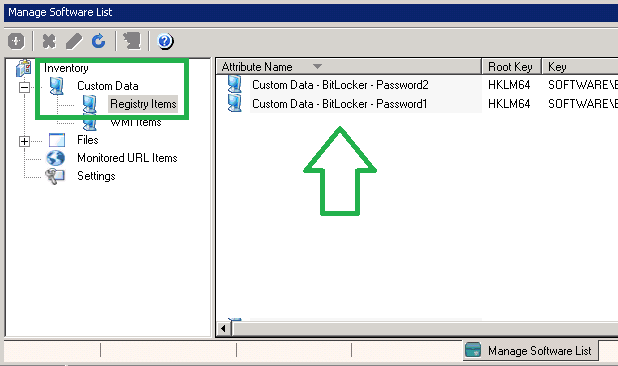
Note, you would have already set up the registry keys on the back end, under Manage Software List – Custom Data – Registry Items.
Manage Software List in LANDesk
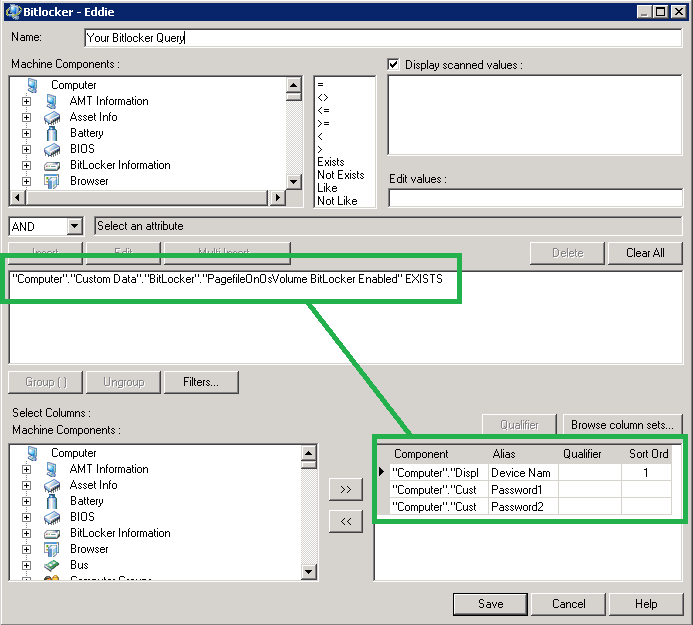
The Bitlocker Query in LANDesk
See also: Create/Import Custom LANDesk Entry into LANDesk Database