When launching one of the Office apps on first login, the user will receive a First things first window. To disable this window, apply the reg keys below.
Screenshot
Single User Method
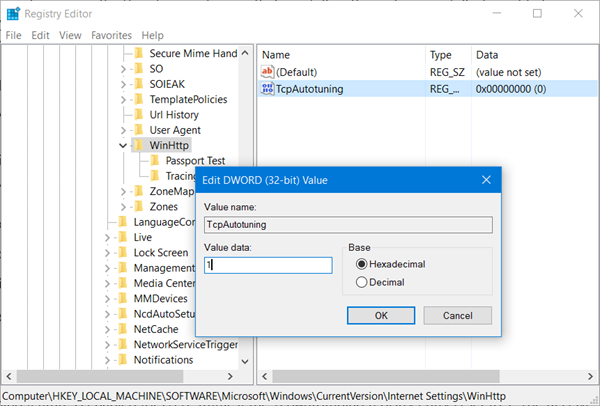
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Office\16.0\Common\General]
“OptInDisable”=dword:00000001
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Office\16.0\Registration]
“AcceptAllEulas”=dword:00000001
* Note, you may need RW permissions to the Microsoft key…if you do, add Authenticated Users with RW permissions.
Default User Profile Method
REG LOAD HKLM\DEFAULT C:\Users\Default\ntuser.dat
REG ADD “HKLM\DEFAULT\SOFTWARE\Policies\Microsoft\Office\16.0\Common\General” /v “OptInDisable” /t REG_DWORD /d 1 /f /REG:64
REG ADD “HKLM\DEFAULT\SOFTWARE\Policies\Microsoft\Office\16.0\Registration” /v “AcceptAllEulas” /t REG_DWORD /d 1 /f /REG:64
REG UNLOAD HKLM\DEFAULT
Or, if you’re really crafty, launch this as admin when the user logs in
on error resume next
Set objShell = CreateObject("Wscript.Shell")
Const HKEY_LOCAL_MACHINE = &H80000002
Const OverwriteExisting = TRUE
'SETS CURRENT DIRECTORY TO VARIABLE
strCurrentDirectory = objShell.CurrentDirectory
'SETS COMPUTER NAME
strComputer = "."
'SET UP WMI
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
'SET UP REGISTRY
Set objRegistry = GetObject("winmgmts:\\" & strComputer & "\root\default:StdRegProv")
strKeyPath = "SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\ProfileList"
objRegistry.EnumKey HKEY_LOCAL_MACHINE, strKeyPath, arrSubkeys
For Each objSubkey In arrSubkeys
on error resume next
strValueName = "ProfileImagePath"
strSubPath = strKeyPath & "\" & objSubkey
objRegistry.GetExpandedStringValue HKEY_LOCAL_MACHINE,strSubPath,strValueName,strValue
Const POPUP_TITLE = "User To SID Conversion"
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set objAccount = objWMIService.Get("Win32_SID.SID='" & objSubkey & "'")
strUser = objAccount.AccountName
'strDomain = objAccount.ReferencedDomainName'returns referenced domain
'PROFILE NAME & SID
objSubkey = trim(objSubkey)'trims whitespace
strUser = trim(strUser)'trims whitespace
'LOGIC TO DETERMINE IF REGISTRY ACCOUNT IS TO BE ACCESSED
if strUser = "SYSTEM" then strUser = ""
if strUser = "LOCAL SERVICE" then strUser = ""
if strUser = "NETWORK SERVICE" then strUser = ""
'if strUser = "Administrator" then strUser = ""
if strUser = "Default" then strUser = ""
if strUser <> "" then
on error resume next
'APPLY REG KEYS
objShell.Run "%comspec% /c reg.exe add "&chr(34)&"HKEY_USERS\" & objSubkey & "\SOFTWARE\Policies\Microsoft\Office\16.0\Common\General"&chr(34)&" /t REG_DWORD /v ""OptInDisable"" /d 1 /f",0,true
objShell.Run "%comspec% /c reg.exe add "&chr(34)&"HKEY_USERS\" & objSubkey & "\SOFTWARE\Policies\Microsoft\Office\16.0\Registration"&chr(34)&" /t REG_DWORD /v ""AcceptAllEulas"" /d 1 /f",0,true
Wscript.Sleep 1000
end if
Next
Notes