I mostly refrain from posting my legal hacking exploits, but…the vendor just hasn’t stepped up to add this feature, and I believe it could be useful to other people.
First, what is RemotePC? RemotePC is a remote access solution for consumers and businesses, and is a product of IDrive Inc. RemotePC allows users, businesses and IT professionals to access and control their PCs & Macs remotely from any device including iOS/Android devices.
In RemotePC, there is a support console (back end), and an agent service (front end). The issue I have with the agent service is it can be configured by the end-user. Why would you allow that??? What company on the planet wants their end-users disabling remote support? None.
So, after contacting the vendor, there is no way to remove the notify icon, which contains all the settings (and, apparently, the remote support functionality). Arrrrrg.
This is what end-users see:
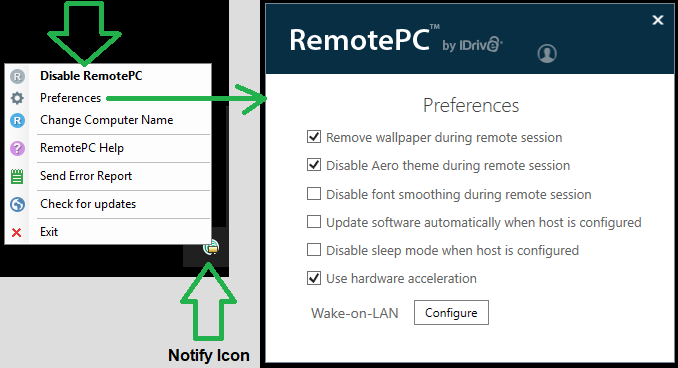
What should be on the menu, and should have the ability to be configured remotely, is a hide icon, but it does not exist.
Okay, on to the hacking part. The first thing I normally do when I want to peer into an application, is to load it into IDA. Interactive Disassembler (or IDA) is a disassembler for computer software which generates assembly language source code from machine-executable code (yes, assembly is still around). It supports a variety of executable formats for different processors and operating systems. It also can be used as a debugger for Windows PE, Mac OS X Mach-O, and Linux ELF executables. Reverse engineering requires practice; it is as much of an artform, as it is a science.
In the IDA Console
After opening IDA, I do an overview of all the code.
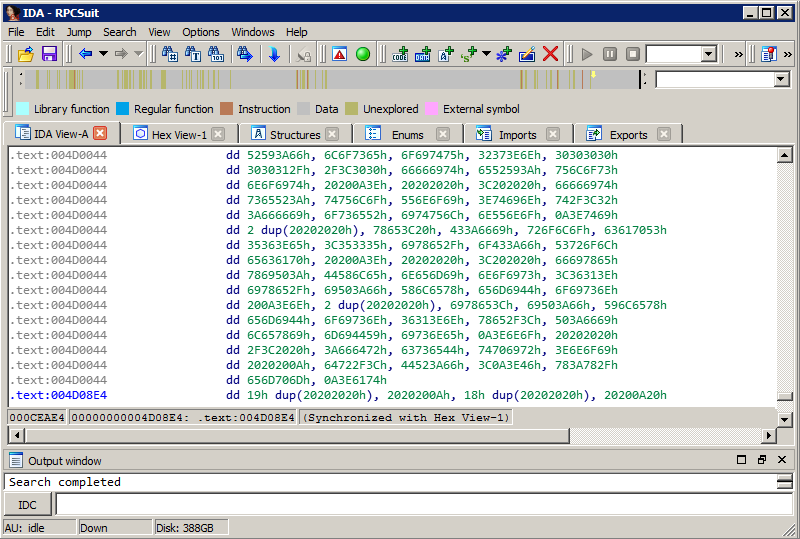
Then, I search for keywords related to my interest. In this case, it is Tray, Icon, Notify. Look what I’m rewarded with just after a couple of searches…

So, armed with this knowledge, I now want to prevent that particular function from being called, or loaded. How do I do that? By simply changing the name of said function, call handler, or program routine. Note, this doesn’t always work the first time (or the second…or the third); it may take numerous searches and attempts, trying different things, to actually modify the code in a manner that doesn’t crash the application. Reverse engineering may also require other tools to assist you in this process, but that’s another story. Never add or remove bits; just replace, as in overwrite, them (if you change the offset, expect the program to crash).
The minor change made:
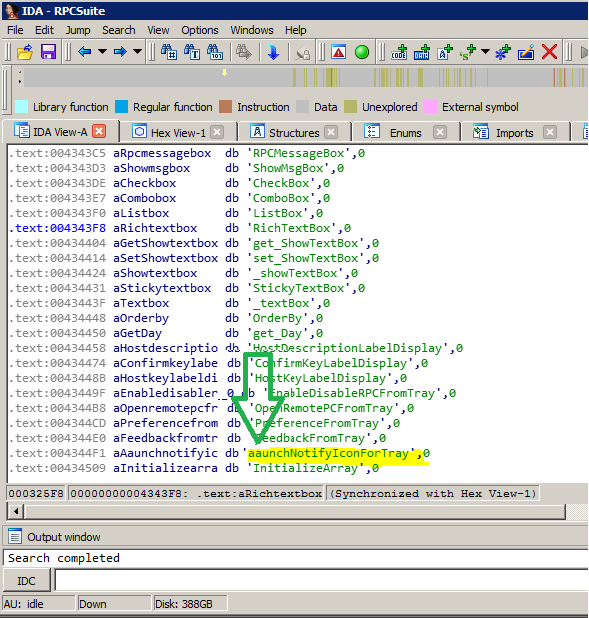
UPDATE 12/19/2018
The company has updated the RPCSuite.exe, thus changing the function in the EXE. Search for INotify now (I changed the ‘I’ to an ‘a’):
![]()
I did the actual mod in another program called Hex Editor Neo. I just like it better for making changes to files.
And, something to think about, you could have added an assembly JMP instruction, effectively hopping over the LaunchNotifyIconForTray, but that requires knowing how to read assembly and doing a live trace (that is a topic for another time). I learned assembly back in the 90’s, and do still use it from time to time. I chose this simpler method, because almost anyone can do it.
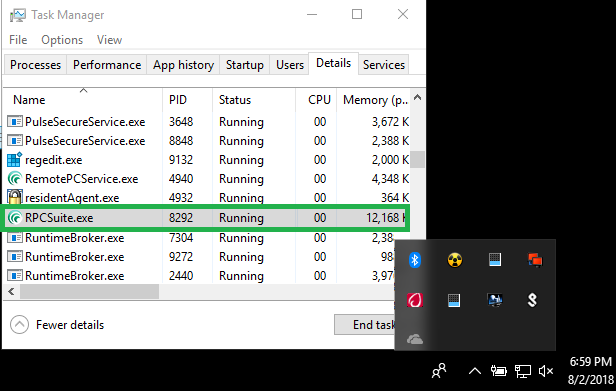
Okay, once that is complete and saved. I run the EXE. The EXE loads just fine, RemotePC works great, and take a look at the icon notification area…no RemotePC notify icon. We did it! We have successfully removed the icon, while maintaining remote support functionality.
Other things I have figured out through reverse engineering
- Removed the toast notification; added one of my own (Vendor, please add this option).
- Added an end-user Allow remote support to connect prompt (Vendor…add this feature).
- Added scan and replace logic to disable AutoUpdates (Would be nice if this was an option).
- For the RemotePC Viewer, I have added 16 new functions.
* sorry, I will not be posting how did these
Notes
Reverse Engineering, or…Reversing
The process of reverse engineering is accomplished by making use of some tools that are categorized into debuggers or disassemblers, hex editors, monitoring and decompile tools:
- Disassemblers – A disassembler is used to convert binary code into assembly code and also used to extract strings, imported and exported functions, libraries etc. The disassemblers convert the machine language into a user-friendly format. There are different dissemblers that specialize in certain things.
- Debuggers – This tool expands the functionality of a disassembler by supporting the CPU registers, the hex duping of the program, view of stack etc. Using debuggers, the programmers can set breakpoints and edit the assembly code at run time. Debuggers analyse the binary in a similar way as the disassemblers and allow the reverser to step through the code by running one line at a time to investigate the results.
- Hex Editors – These editors allow the binary to be viewed in the editor and change it as per the requirements of the software. There are different types of hex editors available that are used for different functions.
- PE and Resource Viewer – The binary code is designed to run on a windows based machine and has a very specific data which tells how to set up and initialize a program. All the programs that run on windows should have a portable executable that supports the DLLs the program needs to borrow from.
Common Tools I use
- Ida Pro
- Windows Tools
- Ollydbg
- gdb
- SimpleProgramDebugger
- Immunity Debugger
- Windbg
- Resource Hacker
- 7-Zip
- HxD Hexeditor
- Hex Editor Neo
- WinInstall by Scalable
- Prism pictaker (takes before & after snapshots)
- x64dbg
- Reko Decompiler
- nasm
- sasm
- PEiD tools
- PE Tools
- Fiddler
- Wireshark
- Procmon
- TCPView
- ProcExp
- file
- nm
- ldd
- otool
- dumpbin
- strings strings
- strip

