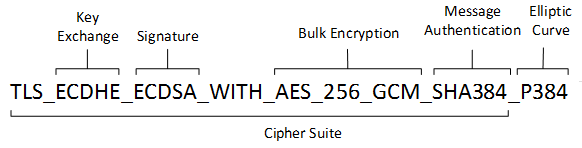
A cipher suite is a set of cryptographic algorithms. The schannel SSP implementation of the TLS/SSL protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks:
- Key exchange
- Bulk encryption
- Message authentication
Key exchange algorithms protect information required to create shared keys. These algorithms are asymmetric (public key algorithms) and perform well for relatively small amounts of data.
Bulk encryption algorithms encrypt messages exchanged between clients and servers. These algorithms are symmetric and perform well for large amounts of data.
Message authentication algorithms generate message hashes and signatures that ensure the integrity of a message.
Developers specify these elements by using ALG_ID data types.
In earlier versions of Windows, TLS cipher suites and elliptical curves were configured by using a single string:
NOTE
Different Windows versions support different TLS cipher suites and priority order. And, some protocol suites are disabled by default in newer operating systems—-causing a support nightmare if you’re using older servers, like Server 2003. Basically, TLS 1.0 is dead; most products have moved to TLS 1.2.
How does TLS work?
Basically, the client and server exchange hellos, compare supported protocols, exchange certificates, and create session keys.
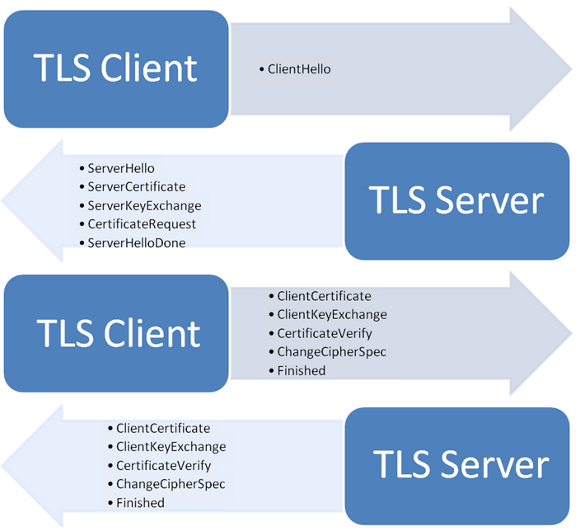
The Handshake
The client sends a client hello message to the server. A client hello message contains the following information:
- ProtocolVersion: The version of the TLS protocol by which the client wants to communicate during this session
- Random: A random structure which contains the current time and date and 28 bytes of a secure random number generated by the client
- SessionID: The ID of a session the client wishes to use for this connection
- CipherSuite: The CipherSuite list which contains the combinations of cryptographic algorithms supported by the client
- CompressionMethod: A list of compression algorithms supported by the client
The server responds with a server hello message in response to a client hello message if it was able to find an acceptable algorithm. A server hello message contains the following information:
- ProtocolVersion: The version of the TLS protocol by which the server agrees to communicate with the client during this session
- Random: A random structure which contains the current time and date and 28 bytes of a secure random number generated by the server
- SessionID: The ID of a session the server wishes to use for this connection
- CipherSuite: The single cipher suite selected by the server from the list of the cipher suite contained in the client hello message
- CompressionMethod: The single compression algorithm selected by the server from the list of the compression method contained in the client hello message.
Immediately after the server sends the server hello message to the client, it sends a server certificate message and a server key exchange message to the client. The certificate request message can optionally be sent by the server to request a certificate from the client if the server chooses to authenticate the client. Then the server sends a server hello done message and will wait for a client to respond.
The client sends a client certificate message to the server if the server requests a certificate in response to the server hello done message. Immediately after the client certificate message is sent, a client key exchange message and a certificate verify message are sent by the client. The client sends a certificate verify message for the server to verify a client certificate.
If the server does not request a certificate, the client key exchange message will be the first message sent by the client. A change cipher spec message and a finished message are sent by the client. In response, the server will send a change cipher specification message and a finished message. At this point, the client and server can exchange application layer data. That should be fairly enough for now to understand overall picture of the protocol.
Cipher Suites
It is important to remember, cipher suites can only be negotiated for TLS versions which support them. The highest supported TLS version is always preferred in the TLS handshake.
Availability of cipher suites should be controlled in one of two ways:
- Default priority order is overridden when a priority list is configured. Cipher suites not in the priority list will not be used.
- Allowed when the application passes SCH_USE_STRONG_CRYPTO: The Microsoft Schannel provider will filter out known weak cipher suites when the application uses the SCH_USE_STRONG_CRYPTO flag. RC4, DES, export and null cipher suites are filtered out.
FIPS-compliance has become more complex with the addition of elliptic curves making the FIPS mode enabled column in previous versions of this table misleading. For example, a cipher suite such as TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 is only FIPS-complaint when using NIST elliptic curves.
For Windows 10, version 1709, the following cipher suites are enabled and in this priority order by default using the Microsoft Schannel Provider:
| Cipher suite | Allowed by SCH_USE_STRONG_CRYPTO | TLS/SSL Version |
|---|---|---|
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 | Yes | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 | Yes | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 | Yes | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 | Yes | TLS 1.2 |
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 | Yes | TLS 1.2 |
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 | Yes | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 | Yes | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 | Yes | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_RSA_WITH_AES_256_GCM_SHA384 | Yes | TLS 1.2 |
| TLS_RSA_WITH_AES_128_GCM_SHA256 | Yes | TLS 1.2 |
| TLS_RSA_WITH_AES_256_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_RSA_WITH_AES_256_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_RSA_WITH_AES_128_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_RSA_WITH_3DES_EDE_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_RSA_WITH_NULL_SHA256
Only used when application explicitly requests. |
No | TLS 1.2 |
| TLS_RSA_WITH_NULL_SHA
Only used when application explicitly requests. |
No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
The following cipher suites are supported by the Microsoft Schannel Provider, but not enabled by default:
| Cipher suite string | Allowed by SCH_USE_STRONG_CRYPTO | TLS/SSL Version |
|---|---|---|
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_DHE_DSS_WITH_AES_256_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_DHE_DSS_WITH_AES_128_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0 |
| TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA | Yes | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_WITH_RC4_128_SHA | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_WITH_RC4_128_MD5 | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_WITH_DES_CBC_SHA | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_DHE_DSS_WITH_DES_CBC_SHA | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_DHE_DSS_EXPORT1024_WITH_DES_CBC_SHA No TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_WITH_NULL_MD5
Only used when application explicitly requests. |
No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_EXPORT1024_WITH_RC4_56_SHA | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_EXPORT_WITH_RC4_40_MD5 | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
| TLS_RSA_EXPORT1024_WITH_DES_CBC_SHA | No | TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0 |
The following PSK cipher suites are enabled and in this priority order by default using the Microsoft Schannel Provider:
| Cipher suite string | Allowed by SCH_USE_STRONG_CRYPTO | TLS/SSL version |
|---|---|---|
| TLS_PSK_WITH_AES_256_GCM_SHA384 | Yes | TLS 1.2 |
| TLS_PSK_WITH_AES_128_GCM_SHA256 | Yes | TLS 1.2 |
| TLS_PSK_WITH_AES_256_CBC_SHA384 | Yes | TLS 1.2 |
| TLS_PSK_WITH_AES_128_CBC_SHA256 | Yes | TLS 1.2 |
| TLS_PSK_WITH_NULL_SHA384 | No | TLS 1.2 |
| TLS_PSK_WITH_NULL_SHA256 | No | TLS 1.2 |
To add cipher suites, either deploy a group policy or use the TLS cmdlets:
- To use group policy, configure SSL Cipher Suite Order under Computer Configuration > Administrative Templates > Network > SSL Configuration Settings with the priority list for all cipher suites you want enabled.
- To use PowerShell, see TLS cmdlets.
NOTE
Prior to Windows 10, cipher suite strings were appended with the elliptic curve to determine the curve priority. Windows 10 supports an elliptic curve priority order setting so the elliptic curve suffix is not required and is overridden by the new elliptic curve priority order, when provided, to allow organizations to use group policy to configure different versions of Windows with the same cipher suites.
General Notes
1 TLS/SSL – How and Why PCI Flags it but why do we care? By: MadHat Unspecific
2 SSL – How and Why What is TLS/SSL? How does TLS/SSL work? What is the difference between TLS and SSL? What is it used for? Weak Ciphers How this relates to PCI Exploitable SSL-Cipher-Check (tool from Unspecific.com)
3 What is TLS/SSL? Transport Layer Security Secure Socket Layers Application Layer Protocols Public/Asymmetric Key Cryptography OSI Layer 6
4 How does TLS/SSL work? Encryption Protocol, Key Length, Hashing Algorithm Authentication Handshake – Request – Protocols Supported – Digital Certificate – Session Keys
5 What is it used for? Security & Data Integrity Prevents Eavesdropping, tampering & message forgery HTTP is most famous as HTTPS Any layer 7 protocol, POP3, IMAP, SMTP, FTP OpenVPN Stunnel Ncat (included with Nmap)
6 Weak Ciphers Old Protocols – SSLv2 Key Strength – 40bit & 56bit ciphers – RC2, RC4, NULL Weak Hash Algorithms – DES ADH – anonymous DH cipher
7 How this relates to PCI & Other Standards PCI 4.1 – Use strong cryptography and security protocols such as SSL/TLS or IPSEC to safeguard sensitive cardholder data during transmission over open, public networks.
8 Exploitable Man in the Middle Decryption of Communications
9 SSL-Cipher-Check OpenSSL binary Checks ALL supported Ciphers openssl ciphers openssl s_client -$protocol -cipher $cipher -connect $host:$port ssl_dump.log Raw openssl output
10 SSL-Cipher-Check $./ssl-cipher-check.pl : SSL Cipher Check: 1.1 : written by Lee ‘MadHat’ Heath (at) Unspecific.com Usage:./ssl-cipher-check.pl [ -dvwas ] [ ] default port is 443 -d Add debug info (show it all, lots of stuff) -v Verbose. Show more info about what is found -w Show only weak ciphers enabled. -a Show all ciphers, enabled or not -s Show only the STRONG ciphers enabled.