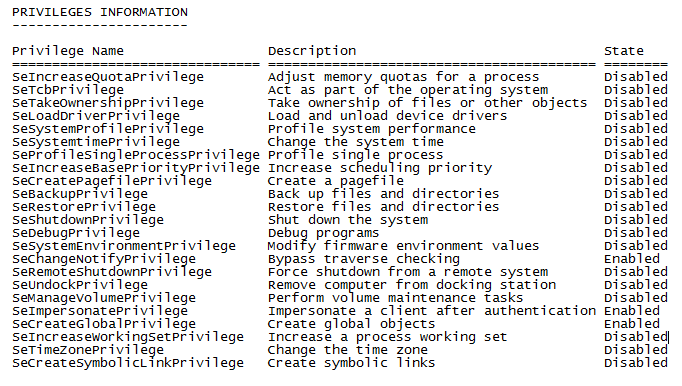
To determine privileges held by a user account, run whoami. This is especially useful when installing SQL, which does an account check.
Command
whoami /priv
Output
Notes
If you’re trying to install SQL, but the account check is failing, you’ll need to either grant domain level privileges or local security privileges to Backup files and directories, Debug Programs, and Manage auditing and security log. I recommend creating a new user account to be utilized as a SQL access account. If there is a domain policy overriding your changes, add the machine’s computer account into an OU that is blocking policy. Then, run gpupdate /force. Check the Local Security Settings on the computer. You should be able to make changes now. Once the changes have been made, run the SQL setup again.
Snapshot of what needs to be updated
Some other random notes
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
The SQL error when TLS 1.0 is disabled
A connection was successfully established with the server, but then an error occurred
during the login process. (provider: Shared Memory Provider, error: 0 – No process is
on the other end of the pipe.)
(Microsoft SQL Server, Error: 233)
SCHANNEL registry status
SSL 2.0: Client: DisabledByDefault = 1 Enabled = 0 Server: DisabledByDefault = 1 Enabled = 0
SSL 3.0: Client: DisabledByDefault = 1 Enabled = 0 Server: DisabledByDefault = 1 Enabled = 0
TLS 1.0: Client: DisabledByDefault = 0 Enabled = 1 Server: DisabledByDefault = 0 Enabled = 1
TLS 1.1: Client: DisabledByDefault = 0 Enabled = 1 Server: DisabledByDefault = 0 Enabled = 1
TLS 1.2: Client: DisabledByDefault = 0 Enabled = 1 Server: DisabledByDefault = 0 Enabled = 1