NOTICE: You’re not going to find this info anywhere on the web, because it’s undocumented. This is experimental, so make backups of your files before editing.
I figured out exactly how the Right-Click Tools work (which is a SCCM add-on), and have added some of my own features and modified some of the original features. In this post, I show you how to expand the Right-Click Tools to include functions you need.
To understand how options are added to the right-click menu, check out the XMLs located here:
C:\Program Files (x86)\Microsoft Configuration Manager\AdminConsole\XmlStorage\Extensions\Actions
If you were to modify those XMLs, options would appear on the menu, though, these options wouldn’t do anything. You would have to add code behind them.
Extra Options
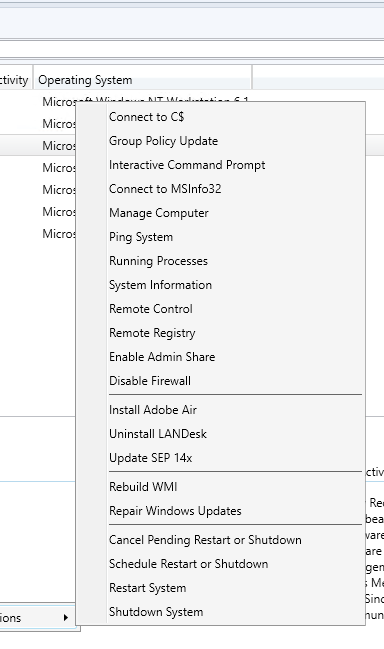
There is a logical flow that the tool follows
1 – The XML File (these are the options that can be seen in the SCCM Console)
2 – SilentOpenPS.vbs or OpenPS.vbs (used to show or hide dialog boxes)
3 – Device – Tools.ps1 (any script which performs an action or function)
Step 1 – Code
Let’s Talk About Code
So, in step 1, you’ll need to add code behind each menu option, before you make the option visible on the menu. Starting with something simple, let’s add the code for the ‘Disable Firewall’ option.
1 – Open Device – Tools.ps1 (located where you installed RCT).
2 – Add this code and save:
"DisableFirewall" {
If ($PSExecLocation.length -gt 1 -and (Test-Path $PSExecLocation)) {
if (Test-Connection -computername $CompName -count 1 -quiet){
& cmd /c "$Directory\psexec.exe" -accepteula "\\$CompName" netsh advfirewall set allprofiles state off
$Popup.Popup("Firewall disabled on $CompName!",0,"Alert",64)
}
else {
$Popup.Popup("$CompName is not online",0,"Error",16)
}
}
else {
$Popup.Popup("PsExec not found.",0,"Error",16)
$ArgList = @()
$ArgList += @("`"$Directory\SilentOpenPS.vbs`"")
$ArgList += @("`"$Directory\Configure Tools.ps1`"")
$ArgList += @("`"Interactive Command Prompt`"")
Start-Process wscript.exe -ArgumentList $ArgList
}
End-Script
}
The magic behind RCT is that it uses psexec to transparently execute remote commands on devices. Clever.
Step 2 – Modify XML
Menu Option
In step 2, once you have completed the coded portion, is to modify relative XML files to make the option visible in SCCM. I modified two XML files.
Main folder
C:\Program Files (x86)\Microsoft Configuration Manager\AdminConsole\XmlStorage\Extensions\Actions
Subfolders
ed9dee86-eadd-4ac8-82a1-7234a4646e62
3fd01cd1-9e01-461e-92cd-94866b8d1f39
Add this XML to each file
* make sure the Right-Click volume and path are correct for your environment
<ActionDescription Class="Executable" DisplayName="Disable Firewall" MnemonicDisplayName="Disable Firewall" Description="Disable Firewall"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters>"D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" ##SUB:ResourceID## ##SUB:__Server## ##SUB:__Namespace## "DisableFirewall"</Parameters> </Executable> </ActionDescription>
Close and reopen the SCCM console.
Test the newly added ‘Disable Firewall’ option on a client machine.
Notes
My XML with other mods
<ActionDescription Class="Executable" DisplayName="Remote Control" MnemonicDisplayName="Remote Control" Description="Remote Control"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - WOL.ps1" ##SUB:ResourceID## ##SUB:__Server## ##SUB:__Namespace##</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Remote Registry" MnemonicDisplayName="Remote Registry" Description="Remote Registry"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters>"D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" ##SUB:ResourceID## ##SUB:__Server## ##SUB:__Namespace## "RemoteRegistry"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Enable Admin Share" MnemonicDisplayName="Enable Admin Share" Description="Enable Admin Share"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters>"D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" ##SUB:ResourceID## ##SUB:__Server## ##SUB:__Namespace## "EnableShare"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Disable Firewall" MnemonicDisplayName="Disable Firewall" Description="Disable Firewall"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters>"D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" ##SUB:ResourceID## ##SUB:__Server## ##SUB:__Namespace## "DisableFirewall"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Separator"> <ShowOn> <string>ContextMenu</string> </ShowOn> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Install Adobe Air" MnemonicDisplayName="Install Adobe Air" Description="Install Adobe Air"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" "##SUB:ResourceID##" ##SUB:__Server## ##SUB:__Namespace## "AdobeAir"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Uninstall LANDesk" MnemonicDisplayName="Uninstall LANDesk" Description="Uninstall LANDesk"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" "##SUB:ResourceID##" ##SUB:__Server## ##SUB:__Namespace## "UninstallLANDesk"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Update SEP 14x" MnemonicDisplayName="Update SEP 14x" Description="Update SEP 14x"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" "##SUB:ResourceID##" ##SUB:__Server## ##SUB:__Namespace## "UpdateSEP"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Separator"> <ShowOn> <string>ContextMenu</string> </ShowOn> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Rebuild WMI" MnemonicDisplayName="Rebuild WMI" Description="Rebuild WMI"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" "##SUB:ResourceID##" ##SUB:__Server## ##SUB:__Namespace## "RebuildWMI"</Parameters> </Executable> </ActionDescription> <ActionDescription Class="Executable" DisplayName="Repair Windows Updates" MnemonicDisplayName="Repair Windows Updates" Description="Repair Windows Updates"> <ShowOn> <string>ContextMenu</string> </ShowOn> <Executable> <FilePath>"wscript.exe"</FilePath> <Parameters> "D:\Right-Click_Tools\SilentOpenPS.vbs" "D:\Right-Click_Tools\Device - Tools.ps1" "##SUB:ResourceID##" ##SUB:__Server## ##SUB:__Namespace## "RepairWinUpdates"</Parameters> </Executable> </ActionDescription>
Just remember the flow:
XML > SilentOpenPS.vbs > WhateverScript.ps1
At this point, you can begin experimenting with your own code.
tags: extending, expanding sccm, sccm tools, MrNetTek