Overview
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many newer computers by the computer manufacturers. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline.
On computers that do not have a TPM version 1.2 or later, you can still use BitLocker to encrypt the Windows operating system drive. However, this implementation will require the user to insert a USB startup key to start the computer or resume from hibernation. Starting with Windows 8, you can use an operating system volume password to protect the operating system volume on a computer without TPM. Both options do not provide the pre-startup system integrity verification offered by BitLocker with a TPM.
In addition to the TPM, BitLocker offers the option to lock the normal startup process until the user supplies a personal identification number (PIN) or inserts a removable device, such as a USB flash drive, that contains a startup key. These additional security measures provide multifactor authentication and assurance that the computer will not start or resume from hibernation until the correct PIN or startup key is presented.
See wiki
Commands and Scripting
Show BitLocker Status
Get-BitLockerVolume -MountPoint “C:”
COMMAND: manage-bde -status C:
Show BitLocker Password
(Get-BitLockerVolume -MountPoint C).KeyProtector.recoverypassword
COMMAND: manage-bde -protectors C: -get
Output BitLocker Password to Text File
(Get-BitLockerVolume -MountPoint C).KeyProtector.recoverypassword | select -Skip 1 | Out-File C:\password.txt
Read BitLocker Text File
$password = Get-Content C:\password.txt
Removing All Protectors (save as script.cmd)
for /f “skip=2 tokens=2 delims=:” %%f in (‘”C:\Windows\system32\manage-bde.exe -protectors -get c:”‘) do (
echo Removing Protector ID:%%f
echo.
“C:\Windows\system32\manage-bde.exe” -protectors -delete c: -id %%f >nul
)
Remove a Single Protector
$BitProtector = Get-BitLockerVolume -MountPoint “C:”
Remove-BitLockerKeyProtector -KeyProtectorId $BitProtector.KeyProtector[1].KeyProtectorId -MountPoint “C:”
Initializing TPM
C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -Command “Initialize-Tpm“
COMMAND: manage-bde -tpm -turnon
See What is TPM?
Enabling TPM – Enable the F1 prompt
enableBitLocker.vbs /on:tpm /l:C:\BitLocker\BitLockerlog.txt
—still looking into a PowerShell method that works
Adding Protector for System Drive
C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -Command “Enable-BitLocker -MountPoint C: -EncryptionMethod Aes128 -UsedSpaceOnly -RecoveryPasswordProtector -SkipHardwareTest”
COMMAND: manage-bde -protectors -add C: -tpm
Enable BitLocker
Enable-BitLocker -MountPoint c: -UsedSpaceOnly -SkipHardwareTest -RecoveryPasswordProtector
COMMAND: manage-bde –on C:
Suspend BitLocker
Suspend-BitLocker -MountPoint “C:” -RebootCount 0
COMMAND: manage-bde –pause C:
Resume BitLocker
Resume-BitLocker -MountPoint “C:”
COMMAND: manage-bde –resume C:
Returning Protector Numerical ID (save as script.cmd)
for /f “skip=2 tokens=2 delims=:” %%g in (‘”C:\Windows\system32\manage-bde.exe -protectors -get c:”‘) do set MyVar=%%g
echo Protector ID:%MyVar%
set MyVar=%MyVar: =%
Verify a BitLocker Password was Returned
SET “var=”&for /f “delims=0123456789-” %%i in (“%Pass%”) do set var=%%i
rem if not matching the delims, exit
if defined var (exit)
Importing BitLocker Password into Active Directory using Numerical ID
C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -Command “Get-BitLockerVolume -MountPoint C: | Backup-BitLockerKeyProtector -KeyProtectorID ‘%MyVar%’ “
Writing BitLocker Password to the Registry (save as script.cmd)
for /f “skip=5 tokens=1 delims=Password ” %%h in (‘”%ThePath%\manage-bde.exe -protectors -get c:”‘) do set Pass=%%h
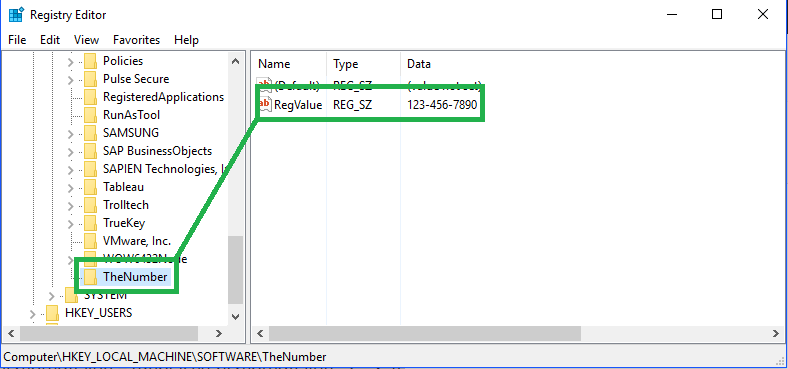
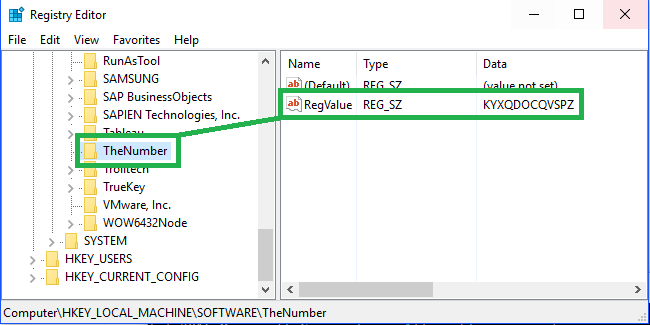
reg.exe add HKEY_LOCAL_MACHINE\SOFTWARE\BitLockerPW /v PW /t REG_SZ /d %Pass% /f /reg:64
Note: If writing BitLocker PW to the registry, a good practice would be to encrypt/obfuscate it.
Note: There is a good chance if you’re compiling your scripts (in a non-64 bit manner), you may need to change from c:\windows\system32 to %windir%\sysnative. The System32 is reserved for 64 bit applications, while the WOW64 will recognize 32 bit applications.
NOTES
Note#1 The TPM chip can store numerous BitLocker IDs and passwords. If this isn’t cleared between computer setups, a new BitLocker password will be appended.
Note#2 If you have key rotation enabled, after a BitLocker password has been once, a new one will be created and securely stored [in SCCM or Azure].
Note#3 As newer Windows operating systems are released, TPM 2.0 (or newer) will become a requirement. This may prompt upgrading your fleet.
Plan for BitLocker management
Deploy BitLocker management
Manage BitLocker policy for Windows 10 in Intune