My disclaimer
Be careful with modifying MOF files—make backups of your DB and relative MOF files before changing them. And, remember…this is the easy portion of the process. There are more advanced topics coming, which include expanding the namespace, merging queries, digging into WMI, modifying classes, and creating stored procedures in SQL. {hey, if it was easy, everyone would be doing it}
Also see: More Advanced Password Handling
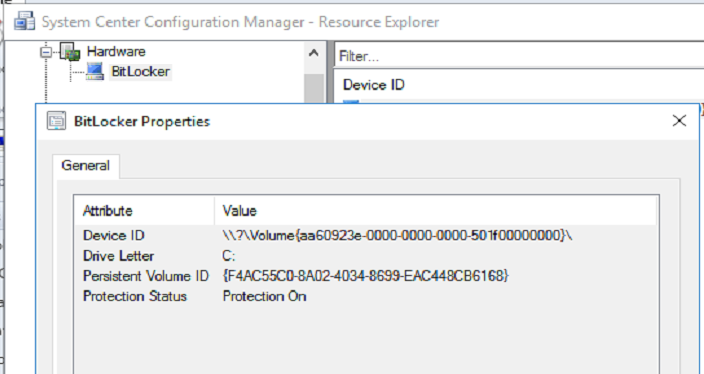
After poking and prodding around in SCCM, I was sure I missed the part where BitLocker passwords could be added to the CM DB, to be easily audited in reports, or used by the support staff. But, upon further research, I realized Microsoft has intentionally left out BitLocker password support to force you to buy MBAM! Ohhhh…Microsoft, say it ain’t so. MS does offer a ‘status’ check for BitLocker, pretty useless, really. Look how anemic it looks…
I thought I would be clever, and ‘hack’ the client portion of MBAM (using the classes from the MSI, I could extrapolate more data, and import that data into the SCCM DB). But, even after all that work…which took a day to figure out, still no BitLocker passwords. Arrrg.
So, by this point, I was done trying to make MBAM work inside of SCCM, without having to actually purchase the product. I moved on to creating my own solution.
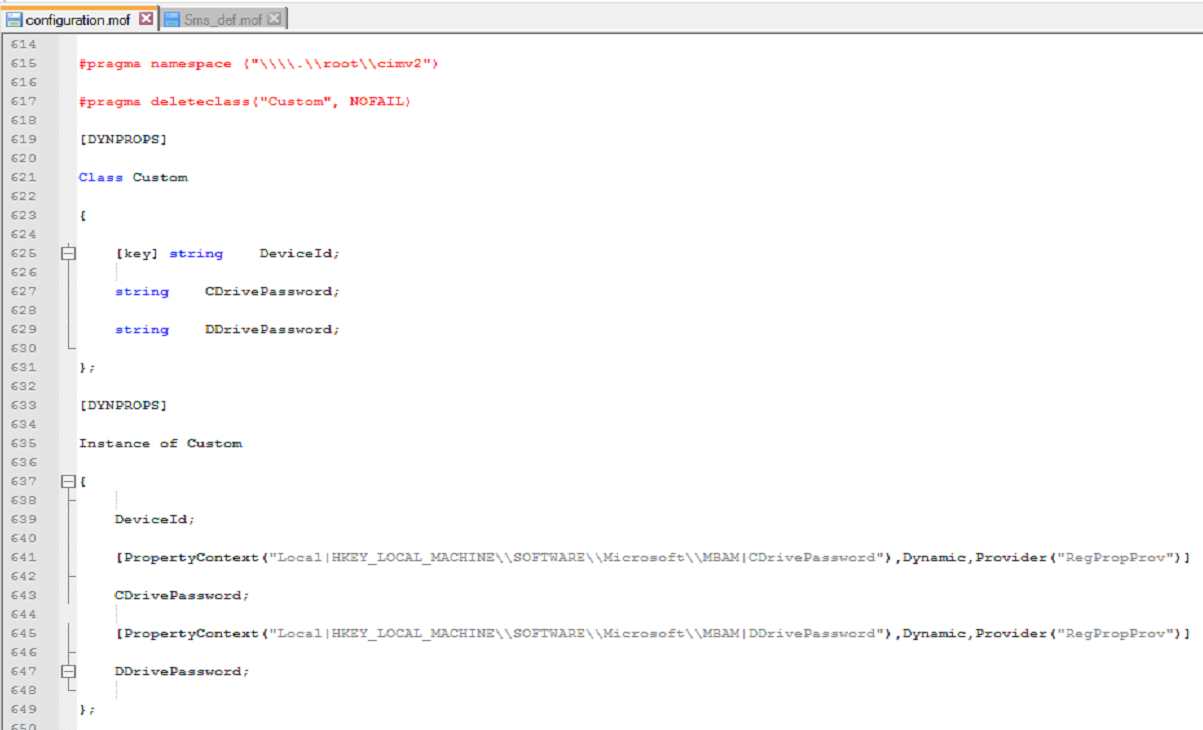
The first step is to modify two MOFs: Configuration and SMS_Def. The MOF format allows you to work with and to change WMI settings. Pretty useful for tweaking or adding inventory items to SCCM. You’re probably going to need help creating these MOFs, so check out: https://www.enhansoft.com/blog/how-to-use-regkeytomof
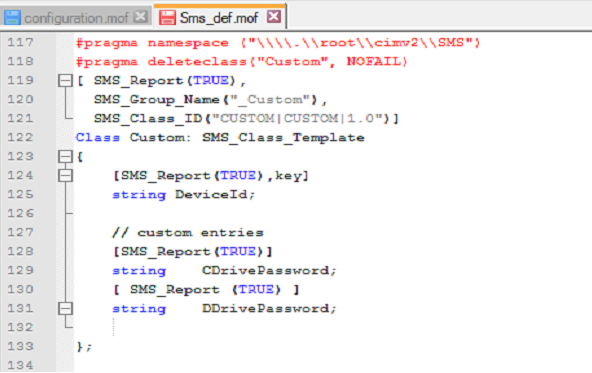
Now, the configuration MOF….
<CMInstallLocation>\Inboxes\clifiles.src\hinv\Configuration.mof
You may have to create this file, <CMInstallLocation>\Inboxes\clifiles.src\hinv\SMS_def.mof
I just added what you see here to the end of a file…and saved. Notice how I’m using the _Custom.
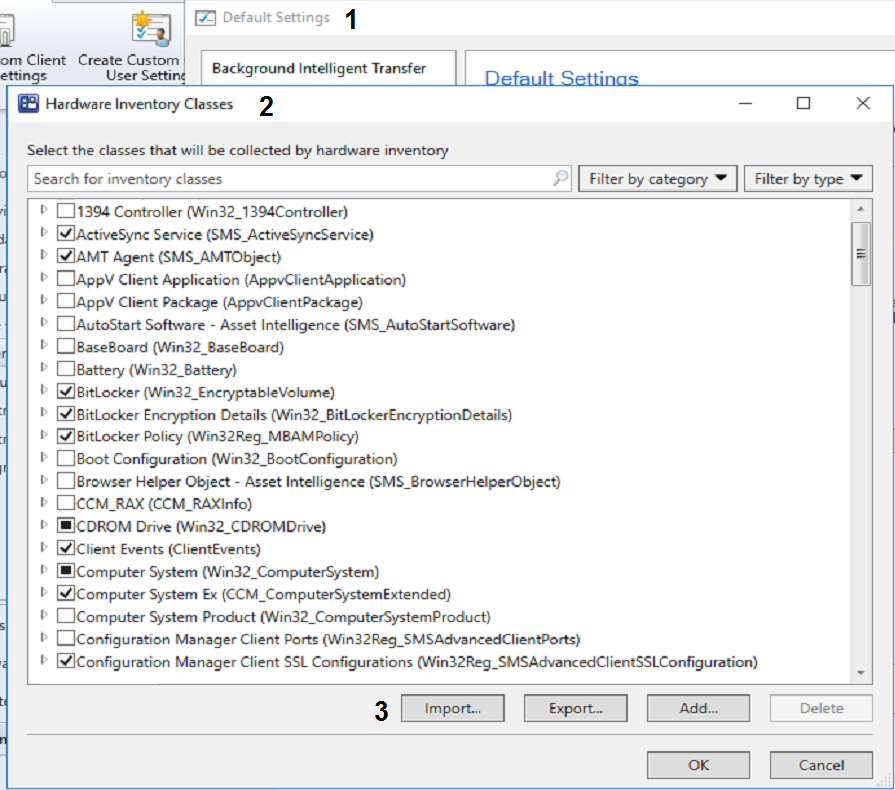
Now, in SCCM, I launched the Client Settings > Default Client Settings, and selected the Hardware Inventory option. I clicked Import and selected the modified SMS_Def.mof file.
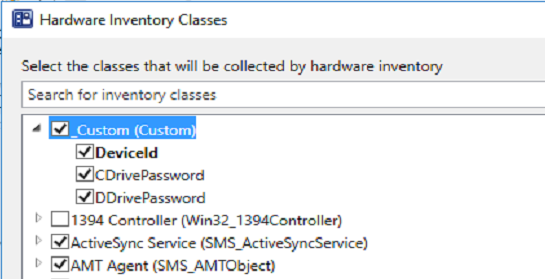
The _Custom class I created appeared at the top. YAY! Okay, things are starting to look up.
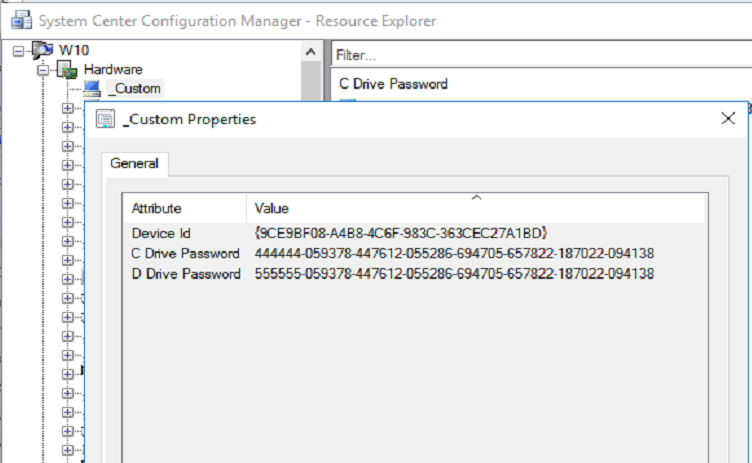
The final thing I did was to force a policy download to a client computer….wait….and then force a hardware inventory scan.
How was I rewarded for my work? I now have BitLocker passwords in SCCM. 🙂
Are you wondering where those passwords came from? I already had a script I created which uses manage-bde to import the BitLocker passwords into the registry. Something I do need to point out: Is storing BitLocker passwords in the registry best practice? Perhaps not. If security is an issue for you, store the passwords in an encoded, obfuscated manner. See this method I created: http://eddiejackson.net/wp/?p=12710
With a little SQL knowledge, the BitLocker data could be encoded while in storage (and while in the local registry), and then decoded when running reports or queries in SCCM (using a SQL stored procedure). Either way, I…we…now have the ability to store and access the BitLocker passwords—without MBAM.
Notes
Next phase will be to add more data to my _Custom table (like data seen from the MBAM client classes (Win32_BitLockerEncryptionDetails and Win32_Reg_MBAMPolicy), but using PowerShell or C#), and work on adding functionality to a BitLocker Node in SCCM. This functionality would hopefully become a MBAM killer. If I get black bagged…send the detectives to Microsoft.
More about MOF: http://liashov.com/wp-content/uploads/2014/01/Start-to-Finish-Guide-to-MOF-Editing.pdf