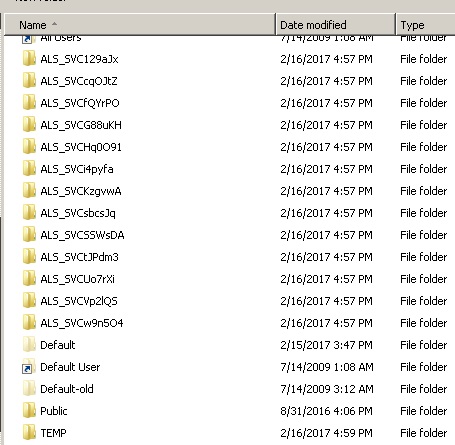
Here is a weird one for you. We’re upgrading to the latest version of LANDesk, and for some reason, numerous LD profile folders are being generated in C:\users (I’m thinking is has to do with the ALS service/LANDesk account). The folders either start with ALS_SVC or TEMP.%computername%.
Two things you’ll need to do
#1 Remove LD profiles from C:\users
#2 Remove LD profiles from the registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
* see updates below
* see Steps to Disable Agentless Scanning, to completely disable it
Screenshot
Solution
Initially, I wrote scripts in PowerShell and VB that looked at folder size and removed 0 byte sizes, the problem was…while they worked in other folders just fine, they could not read all of the C:\users folders—-no access (certain vb and ps objects just could not access the folders). So, I went low tech with this one. And, guess what? It worked. I wrote this batch and compiled it into an EXE. Once launched, it found the 0 byte size folders and removed them.
@echo off
title LANDesk Cleanup
setlocal enabledelayedexpansion
set DName=
set FSize=0
C:
cd\users
:: return objects in directory
for /f “tokens=*” %%A in (‘dir c:\users /a /b’) do (
set DName=c:\users\%%A
echo Checking !DName!…
:: scan through all folders
:: set total size of folder to cumulative file sizes
for /f “tokens=3-4” %%B in (‘dir “!DName!” /s ^| find /i “file(s)”‘) do (
set FSize=%%B
)
:: if no files were returned, this directory has a size 0
:: if size 0, then remove folder and all subfolders
:: log the action
if !FSize! EQU 0 rd /q /s “!DName!” && echo %Date% !DName! !FSize!>>C:\users\removal_log.txt
echo.
)
endlocal
* Update 02/20/2017
So, come to find out, NOT all the LANDesk profile folders were 0 byte. So, I ended up writing a new script to just delete ALS_SVC* and TEMP.* folders
@echo off
title LANDesk Cleanup
setlocal enabledelayedexpansion
c:
cd\users
cls
set DName=
set FSize=
set CName=%computername%
set str1=ALS_SVC
set str2=TEMP.
set found=false
:: GET FOLDER
For /d %%A in (*) Do (
set found=false
set DName=c:\users\%%A
:: UPDATE TIMESTAMP
for /F “TOKENS=*” %%T in (‘Time /t’) do set NowT=%%T
:: FIND FOLDER SIZE
for /f “tokens=3-4” %%S in (‘dir “!DName!” /s ^| find /i “file(s)”‘) do set FSize=%%S
:: DELETE ALS_SVC*
echo %%A | find /i “%str1%”>nul && (
echo DELETE: “!DName!”
rd /q /s “!DName!” && echo DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
set found=true
)
:: DELETE TEMP.*
echo %%A | find /i “%str2%”>nul && (
echo DELETE: “!DName!”
rd /q /s “!DName!” && echo DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
set found=true
)
IF NOT ALS OR TEMP, LOG
if !found! EQU false echo NOT_DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
)
set DName=
set FSize
set CName=
set str1=
set str2=
endlocal
exit /b 0
* Update 02/21/2017
Yet another update. It was requested that the amount of folders being deleted, a timestamp of the last run date of the deployment package, and total times the package has run, all be tracked. So, I modified the script above to add counters for the package and for the folders being deleted. These variables are added to the registry, which are then scanned via our desktop management software.
The reg keys that are added
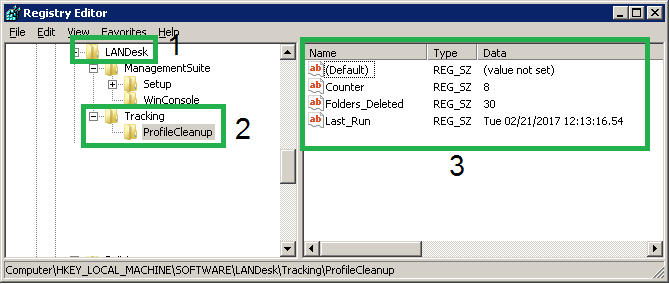
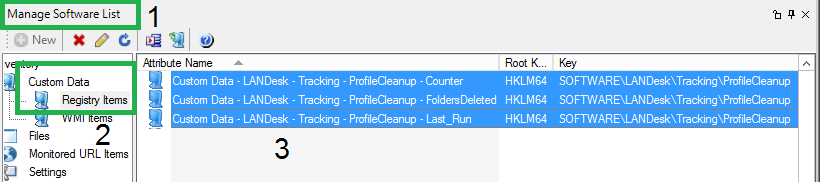
In LANDesk, these are published to clients
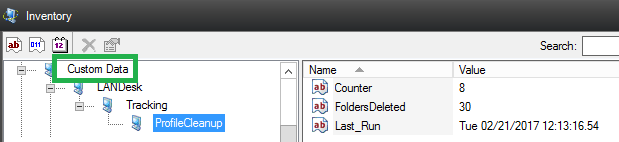
The final result, an updated inventory record with tracking info
The modified script – this was compiled
@echo off
title LANDesk Cleanup
setlocal enabledelayedexpansion
c:
cd\users
cls
:: folders to look for
set str1=ALS_SVC
set str2=TEMP.
:: directory name
set DName=
:: directory size
set FSize=
:: bool: if folder matches logic
set found=false
set fCount=
set rCount1=0
set rCount2=0
:: reg key
set AppName=ProfileCleanup
set RegKey1=”HKLM\SOFTWARE\LANDesk\Tracking\%AppName%” /v “Counter”
set RegKey2=”HKLM\SOFTWARE\LANDesk\Tracking\%AppName%” /v “Last_Run”
set RegKey3=”HKLM\SOFTWARE\LANDesk\Tracking\%AppName%” /v “Folders_Deleted”
:: REMOVE ALL ALS_SVC* FOLDERS
For /d %%A in (*) Do (
set found=false
set DName=c:\users\%%A
for /F “TOKENS=*” %%T in (‘Time /t’) do set NowT=%%T
for /f “tokens=3-4” %%S in (‘dir “!DName!” /s ^| find /i “file(s)”‘) do set FSize=%%S
echo %%A | find /i “%str1%”>nul && (
echo DELETE: “!DName!”
rd /q /s “!DName!” && echo DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
set found=true
set /a fCount+=1
)
echo %%A | find /i “%str2%”>nul && (
echo DELETE: “!DName!”
rd /q /s “!DName!” && echo DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
set found=true
set /a fCount+=1
)
if !found! EQU false echo NOT_DELETED %Date% !NowT! “!DName!” !FSize!>>c:\users\removal_log.txt
)
:: if counter key doesn’t exist, create it
%windir%\sysnative\REG QUERY %RegKey1%
if %ERRORLEVEL% EQU 0 goto :Main
if %ERRORLEVEL% EQU 1 goto :Add
ping -n 4 127.0.0.1>nul
:Add
cls
echo Key not found. Adding Key…
%windir%\sysnative\REG ADD %RegKey1% /d 0 /reg:64 /f
%windir%\sysnative\REG ADD %RegKey3% /d 0 /reg:64 /f
ping -n 4 127.0.0.1>nul
:: retrieve current count and add 1
:: this is how many times the script has run
:Main
cls
echo Retrieving Reg Count…
FOR /f “tokens=1,2,3” %%a In (‘%windir%\sysnative\REG QUERY %RegKey1% /reg:64’) do (
set rCount1=%%c
set /a rCount1+=1 && %windir%\sysnative\REG ADD %RegKey1% /d !rCount1! /reg:64 /f
ping -n 4 127.0.0.1>nul
)
:: this is how many folders have been deleted
cls
echo Retrieving Folder Count…
FOR /f “tokens=1,2,3” %%a In (‘%windir%\sysnative\REG QUERY %RegKey3% /reg:64’) do (
set rCount2=%%c
set /a “rCount2=!rCount2!+!fCount!” && %windir%\sysnative\REG ADD %RegKey3% /d !rCount2! /reg:64 /f
)
:: add timestamp to registry
%windir%\sysnative\REG ADD %RegKey2% /d “%date% %time%” /reg:64 /f
:: clear session
set RegKey1=
set RegKey2=
set RegKey3=
set fCount=
set rCount1=
set rCount2=
set AppName=
set DName=
set FSize
set str1=
set str2=
set NowT=
:: clean up registry keys
cls
echo Removing LANDesk ALS profiles…
for /f “tokens=1,2 delims==” %%s IN (‘WMIC path win32_useraccount where name^=’administrator’ get sid /value ^| find /i “SID”‘) do set SID=%%t
set RootSID=%SID:~0,-5%
set RegPath=HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
set /a counter=3
:loop1
if %counter% lss 10 (
reg delete “%regPath%\%RootSID%-100%counter%” /f /reg:64
set /a counter+=1
goto :loop1
)
set /a counter=10
:loop2
if %counter% lss 100 (
reg delete “%regPath%\%RootSID%-10%counter%” /f /reg:64
set /a counter+=1
goto :loop2
)
set /a counter=100
:loop3
if %counter% lss 999 (
reg delete “%regPath%\%RootSID%-1%counter%” /f /reg:64
set /a counter+=1
goto :loop3
)
endlocal
exit /b 0
* Note how %windir%\sysnative was used. You’ll use %windir%\system32 if using a 64bit compiler or running script not compiled
Notes
As for what’s causing the issue, beyond the ALS account, LANDesk is still trying to figure it out.

Some C# code I was working on to do the task above.
using System;
using System.Collections.Generic;
using System.IO;
using System.Linq;
class LANDeskProfileCleanup
{
public static void Main(string[] args)
{
try
{
string dirPath = @"c:\users\";
List<string> dirs List<string>(Directory.EnumerateDirectories(dirPath));
foreach (var dir in dirs)
{
long length = Directory.GetFiles(dir, "*", SearchOption.AllDirectories).Sum(t =&amp;gt; (new FileInfo(t).Length));
Console.WriteLine("{0}", dir.Substring(dir.LastIndexOf("\\") + 1));
}
//Console.WriteLine("{0} Folders found.", dirs.Count);
}
catch (UnauthorizedAccessException UAEx)
{
Console.WriteLine(UAEx.Message);
}
catch (PathTooLongException PathEx)
{
Console.WriteLine(PathEx.Message);
}
Console.ReadLine();
}
public static long DirSize(DirectoryInfo dir)
{
return dir.GetFiles().Sum(fi => fi.Length) +
dir.GetDirectories().Sum(di => DirSize(di));
}
}