Microsoft has released a security update to address a vulnerability in implementations of Server Message Block 1.0 (SMBv1). Exploitation of this vulnerability could allow a remote attacker to take control of an affected system.
US-CERT encourages users and administrators to review Microsoft Security Bulletin MS17-010 and apply the update. For more information, see the Information Assurance Advisory and US-CERT’s SMB Security Best Practices guidance.
Note, ever since Windows 10 Build 1709, the reg keys don’t work so great (that’s because MS has removed the SMBv1 feature, altogether). Use dism or PowerShell cmdlets instead.
Return all protocols
dism /online /get-features /format:table
Enable SMBv1 via PowerShell
Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol -norestart
Enable SMBv1 via Dism
dism /online /enable-feature /featurename:SMB1Protocol-Server -NoRestart
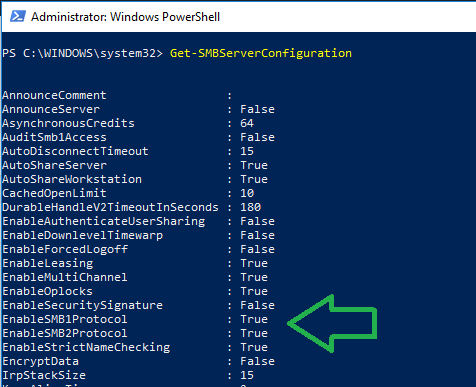
To check the status of SMB versions on your servers (from PowerShell)
Get-SMBServerConfiguration
Snapshot
This is the reg key for SMBv1:
Steps to enable and disable the SMBv1 on the SMB server using the registry:
Registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
For SMBv2…
Registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
Notes
https://technet.microsoft.com/en-us/library/security/mt745122.aspx
Other Bulletins (yes, you should be reading these)
https://technet.microsoft.com/en-us/library/security/mt745122.aspx
Commands
Disables the SMBv1 on the SMB client by running the below commands
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabled
Enables the SMBv1 on the SMB client by running the below commands
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb10 start= auto
Disables the SMBv2 and SMBv3 on the SMB client by running the below commands
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi
sc.exe config mrxsmb20 start= disabled
Enables the SMBv2 and SMBv3 on the SMB client by running the below commands
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb20 start= auto
Script to Disable SMB
@echo off
Title Manage SMB
cls
:DISABLE
%windir%\system32\sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi >log.txt
%windir%\system32\sc.exe config mrxsmb10 start= disabled >>log.txt
%windir%\system32\sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi >>log.txt
%windir%\system32\sc.exe config mrxsmb20 start= disabled >>log.txt
%windir%\system32\EVENTCREATE.exe /T INFORMATION /l Application /ID 777 /d “Disabled SMB”
exit
PowerShell
Disables the SMBv1 on the SMB server by running the below command
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” SMB1 -Value 0 –Force
Disables the SMBv2 and SMBv3 on the SMB server by running the below command
Set-ItemProperty –Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” SMB2 –Value 0 –Force
Enables the SMBv1 on the SMB server by running the below command
Set-ItemProperty –Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” SMB1 –Value 1 –Force
Enables the SMBv2 and SMBv3 on the SMB server by running the below command
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” SMB2 -Value 1 -Force